One Click to Zero Trust: How Cato’s Agentless Microsegmentation Blocks Lateral Movement and Simplifies Network Security
One click on a malicious email. One compromised device. That’s often all it takes for malware or ransomware to spread across an entire network in minutes. In other cases, attackers move silently for months before striking. Cato’s agentless microsegmentation stops lateral movement at its source, isolating each device and preventing threats from spreading before they cause real damage.
The Challenge: Why Microsegmentation Matters Across the Entire Organization from IT and OT to AI and Every VLAN
Modern threats and advanced persistent attackers no longer stop at breaching the perimeter. They move laterally across flat networks and shared VLANs, often using stealthy techniques like LOLBins and LoLScripts to stay hidden for months. During that time, they escalate privileges, exfiltrate data, deploy ransomware, or disrupt critical OT systems. As we noted in our OT protection blog, segmentation between IT and OT is a key recommendation from both CISA and NIST SP 800-82 to reduce risk and control east-west traffic in operational environments.
But it’s not just malware we need to defend against. As AI agents become more embedded in production systems, they introduce new risk, whether from malicious use or unintended actions. Without proper segmentation, one misconfigured or compromised AI agent could unintentionally trigger a chain reaction across an entire network. Microsegmentation provides the guardrails needed to contain these risks, ensuring secure, isolated execution across both human and machine-driven environments.
Cato’s Answer: Agentless Microsegmentation That Works at the Click of a Button
That’s why Cato has built agentless microsegmentation into the Cato SASE Cloud Platform, turning a previously complex task into a simple, policy-driven action.
You can enable it:
- Per VLAN through the Cato Management Application (CMA),
- Or globally across all VLANs via the Cato API.
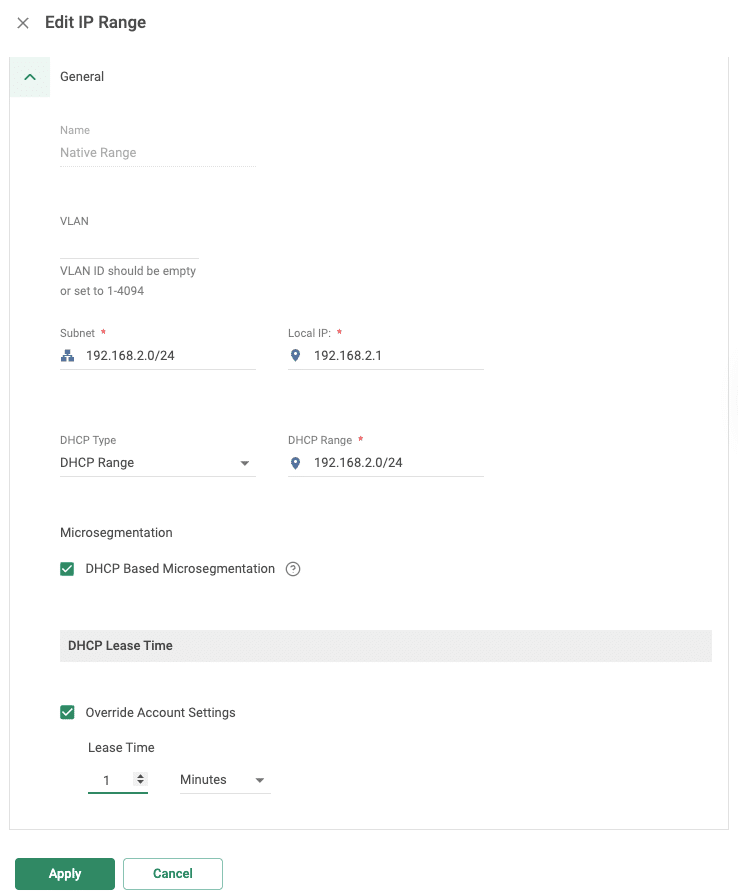
Once enabled, every device is assigned a /32 subnet through DHCP. This isolates hosts at Layer 2, forcing intra-VLAN (east-west) traffic to pass through the Cato Socket, where our Next-Gen LAN Firewall inspects and enforces policy. In Figure 1 you can see how simple is to click the checkbox and enable microsegmentation for your vlan, then you can easly setup proper and relevant FW rules in addition as nessary.
Figure 1. Configuring Microsegmentation in CMA
The result: Devices can only communicate with their gateway, no peer-to-peer exposure, no lateral reconnaissance, no stealthy spread.
Go Beyond Threat Prevention: A Simpler, Smarter Path to Zero Trust
Security isn’t just about blocking threats, it’s about doing so without breaking operations.
With Cato:
- There’s no agent to deploy, and no host-based enforcement to manage.
- You don’t need to fragment your network with dozens of VLANs.
- Policy enforcement is centralized, visual, and consistent across all sites.
Microsegmentation becomes an extension of your Zero Trust strategy, applied uniformly, whether you’re protecting a remote branch, a core data center, or an OT network. And unlike other tools that detect lateral movement after a breach, Cato blocks it by design, while still allowing selective isolation through our firewall. If a device tries to reach out to a botnet C&C or shows anomalous behavior, we can:
- Dynamically block outbound attempts, or
- Isolate it from the internet entirely, while preserving internal monitoring access, as recommended for OT environments.
One Platform, Total OT Protection | Read the blog
Future-Proofing AI, IoT, and OT: Microsegmentation for the Next Generation of Infrastructure
Gartner highlights microsegmentation as a key capability for reducing risk by limiting lateral movement, isolating workloads, and adapting to modern, dynamic environments. This includes support for virtualized deployments, automation in CI/CD pipelines, and protection for IoT and OT infrastructure.
Cato addresses these needs through:
- Agentless workload isolation using automatic /32 subnetting and granular firewall enforcement,
- Full API and Terraform support for integrating microsegmentation into CI/CD workflows and infrastructure automation,
- Visibility across north-south and east-west traffic flows to inform policy decisions,
- Support for virtualized environments and dynamic onboarding of assets across all VLANs,
- Built-in protection for OT and IoT devices, without the need for local agents or complex NAC setups see also our previous blog post on OT protection .
- Device inventory and asset discovery
Cato delivers a practical, scalable, and unified approach that meets the majority of enterprise use cases, all within the Cato SASE Cloud platform.
One Unified Platform: Replace NAC, Simplify Segmentation, Enable Zero Trust
Traditional NACs fall short. They require agents, hardware, and complex onboarding. They often can’t keep up with cloud or hybrid environments.
With Cato, you get:
- Agentless, scalable segmentation in minutes,
- Policy-based control without VLAN sprawl,
- Cloud-native enforcement across your entire SASE fabric.
No bolt-ons. No complexity. Just true microsegmentation as part of a consolidated Zero Trust architecture.
Start Small, Scale Fast, and Cut Off Lateral Threats Today
Cato recommends starting with a single VLAN range and adjusting DHCP lease time to expedite deployment. You can monitor impact, tune policy, and scale organization-wide, all from a single interface.
Security teams get peace of mind. IT teams get their time back. And your network becomes dramatically more resilient, to ransomware, insider threats, AI errors, and OT attacks alike.
The post One Click to Zero Trust: How Cato’s Agentless Microsegmentation Blocks Lateral Movement and Simplifies Network Security appeared first on Cato Networks.