Mitigating Credential Phishing in the Age of AI and Cloud Convergence
Phishing remains one of the most effective methods for stealing credentials and breaching enterprise environments. Despite advanced email and browser protections, attackers now leverage AI, and automation to outpace traditional defenses. The Verizon 2024 Data Breach Investigations Report found that 68% of breaches involve the human element, often triggered within seconds of a phishing lure, just 21 seconds to click and 28 seconds to submit credentials. Today’s phishing campaigns extend beyond deceptive emails to fake SaaS portals, malicious file shares, and AI-crafted impersonations that exploit user trust across cloud platforms. Cato Networks helps organizations mitigate this evolving threat through a converged, inline, and context-aware SASE platform that detects, contains, and correlates phishing activity across all traffic flows.
The New Face of Phishing: From Deception to Automation
Traditional phishing relied on social engineering and human error. Today, threat actors are scaling deception through AI-generated content, cloned SaaS portals, and malicious automation that make attacks faster and more convincing.
Many modern campaigns exploit legitimate cloud infrastructure, a tactic known as “Living off the Cloud,” malicious payloads on platforms like Google Drive, SharePoint, or Trello. Others use newly registered domains (NRDs) and TLS encryption to hide payloads and evade detection.
Gartner predicts that by 2027, AI agents will reduce the time it takes to exploit account exposures by 50%, underscoring how automation now accelerates credential abuse at machine speed.
A recent Cato CTRL investigation revealed how threat actors leveraged AI marketing platform host realistic Microsoft 365 phishing portals, stealing corporate credentials from unsuspecting users. This illustrates the convergence of AI and social engineering, and how traditional defenses often fail to keep up.
Threat Actors Abuse Simplified AI to Steal Microsoft 365 Credentials | Read the blog
Why Phishing Detection Is Harder Than Ever
Even advanced enterprises struggle to identify phishing in time because of four growing challenges:
- Newly Registered Domains (NRDs): Constantly shifting infrastructure makes reputation-based blocking ineffective.
- Encrypted Traffic: TLS hides phishing forms and payloads in legitimate HTTPS sessions.
- SaaS Abuse: Attackers exploit legitimate cloud services to host fake login pages.
- Fragmented Visibility: Point products can’t correlate events across email, network, and identity layers.
Gartner predicts that by 2028, 25% of organizations will adopt secure enterprise browsers to enhance remote access and endpoint security. Cato addresses the same underlying challenge through Remote Browser Isolation (RBI) and ZTNA (via the Cato Browser Extension or ZTNA client). Together, these capabilities apply policy controls and inspection to browser traffic, helping prevent credential submission on untrusted or AI-generated sites. By executing web sessions in a secure, cloud-based container, RBI delivers the safe browsing and data-protection outcomes envisioned by Gartner, without requiring organizations to deploy or manage a new browser.
Cato’s Converged Anti-Phishing Architecture
Cato’s approach to phishing defense is layered, correlated, and continuous, combining inline inspection, behavioral analytics, and unified visibility. This enables mitigation at every stage of the phishing lifecycle.
Cato mitigates credential phishing through a continuous, multi-stage defense lifecycle that unifies prevention, detection, and rapid containment. As shown in Figure 1, threats are intercepted at multiple layers:
- Access Blocked: Initial access is blocked through threat prevention (DNS Security, Firewall-as-a Service (FWaaS), and IPS)
- Credential Submission Prevented: Credential submission is identified and isolated also by threat prevention (IPS and RBI)
- Response and Containment: Security is further reinforced with application and data protection (Cloud Access Security Broker (CASB) by restricting risky user actions within SaaS applications, preventing attackers from abusing cloud services during or after an attack. Suspicious Activity Monitoring (SAM) and XOps detect post-compromise anomalies and correlate them across the network, while DLP prevents potential data exfiltration.
- Post-Compromise Detected: Swift user isolation and real-time policy updates to contain the threat are enabled by CMA and EDR integrations.
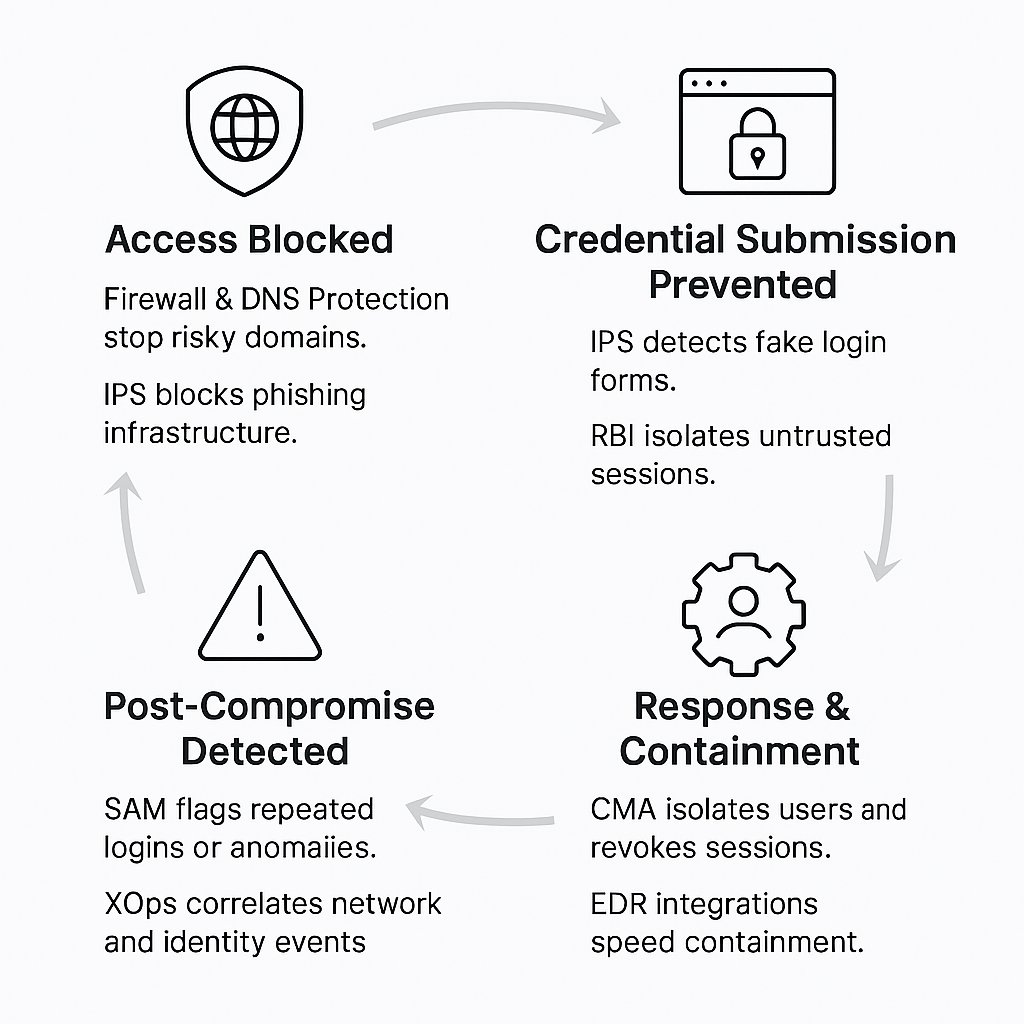
Figure 1. The Credential Phishing Mitigation Lifecycle
Cato’s unified defenses work in a continuous loop, blocking access, preventing credential submission, detecting post-compromise activity, and containing incidents in real time.
Core Protections in Action
Cato integrates multiple security engines that operate in parallel to detect and contain phishing at scale. Each layer contributes unique visibility and control across web, cloud, and access traffic.
Unified, Inline Protection, From Access to Response
Unlike point products that inspect traffic in isolation, Cato inspects all WAN, Internet, and remote access traffic inline within each PoP.
All detections, from Internet Firewall, IPS, DNS Protection, CASB, ZTNA, and RBI, feed into XOps, which correlates them into unified “Security Stories.”
Through the Cato Management Application (CMA), security teams can visualize phishing-related events, drill down into user sessions, and enforce new policies instantly, without switching between consoles or tools.
Cato’s cross-engine correlation enables faster understanding of the full attack flow, turning multiple alerts into a single, actionable narrative.
Mitigating the Unstoppable
No organization can stop phishing completely. But by consolidating inspection, identity, and analytics into one cloud-native architecture, Cato reduces risk, accelerates detection, and minimizes the impact of credential theft.
With AI-driven detection, secure browser isolation, and unified visibility, Cato transforms the fight against phishing from reactive to proactive. Phishing resilience isn’t about blocking every link, it’s about detecting intent, limiting exposure, and containing compromise before it spreads.
Explore more related Blog posts from Cato CTRL:
- Cato CTRL: Suspected Russian Threat Actors
- Threat Actors Abuse Simplified AI to Steal Microsoft 365 Credentials
For a deeper technical overview and configuration guidance, visit our Cato Anti-Phishing Protections Knowledge Base article
The post Mitigating Credential Phishing in the Age of AI and Cloud Convergence appeared first on Cato Networks.
 Threat Report | Download the report
Threat Report | Download the report