Cato CTRL™ Threat Research: Overview of BloodHound and Associated Collectors Including ShadowHound, SharpHound, and SoapHound
Executive Summary
Think back to when you were a kid, eyeing a cookie jar on the top shelf. Getting to it wasn’t just about reaching; it was about strategy. You had to avoid making noise, pick the sturdiest route, and time your move perfectly to avoid getting caught. Imagine having a team of expert scouts feeding you all the correct information: where the dangers are, which surfaces can support you, and the best way to grab that prize unnoticed. That’s exactly what BloodHound does. BloodHound is an attack path management (APM) solution used to analyze and visualize Active Directory (AD) relationships and permissions to identify potential attack paths within a network.
The BloodHound team developed SharpHound, while third-party open-source contributors created other collector tools, including SoapHound and ShadowHound. Collector tools like SharpHound, SoapHound, and ShadowHound gather data on AD objects and relationships using a variety of protocols, including Lightweight Directory Access Protocol (LDAP), Server Message Block (SMB), and Active Directory Web Services (ADWS). These collector tools enable security teams to map complex environments accurately, allowing threat actors to navigate through the victim environment to reach their end goal, whether obtaining domain admin credentials, collecting sensitive data from databases, or other goals.
BloodHound is more than just an APM solution; it’s a strategic asset. Recognized in frameworks like MITRE ATT&CK, it’s been used by threat groups including the Ryuk ransomware gang, the Play ransomware gang, Ember Bear, and Cozy Bear. Their value in such a tool isn’t just in seeing the environment; it’s in understanding where the victim’s gaps are and how to move through them with precision.
We will break down BloodHound and its associated collectors: how they gather data, what makes each one effective, how they’re built to evade detection, and what defenders should look for to catch them in action and use them to find such misconfigurations or overprivileged accounts.
Technical Summary
The Hound Breeds: A Tactical Overview
BloodHound is a reconnaissance tool that visualizes AD relationships like user-group memberships, logon sessions, permissions, and trust paths. Using it, threat actors can identify and map potential privilege escalation routes within a Windows domain. BloodHound relies on collectors, such as SharpHound, SoapHound, and ShadowHound, that gather data across various protocols to reveal hidden connections and attack paths. Each specializes in gathering specific intel about users, groups, and network connections.
Below is a demonstration of how threat actors can benefit from utilizing BloodHound.
SharpHound: The Core Collector
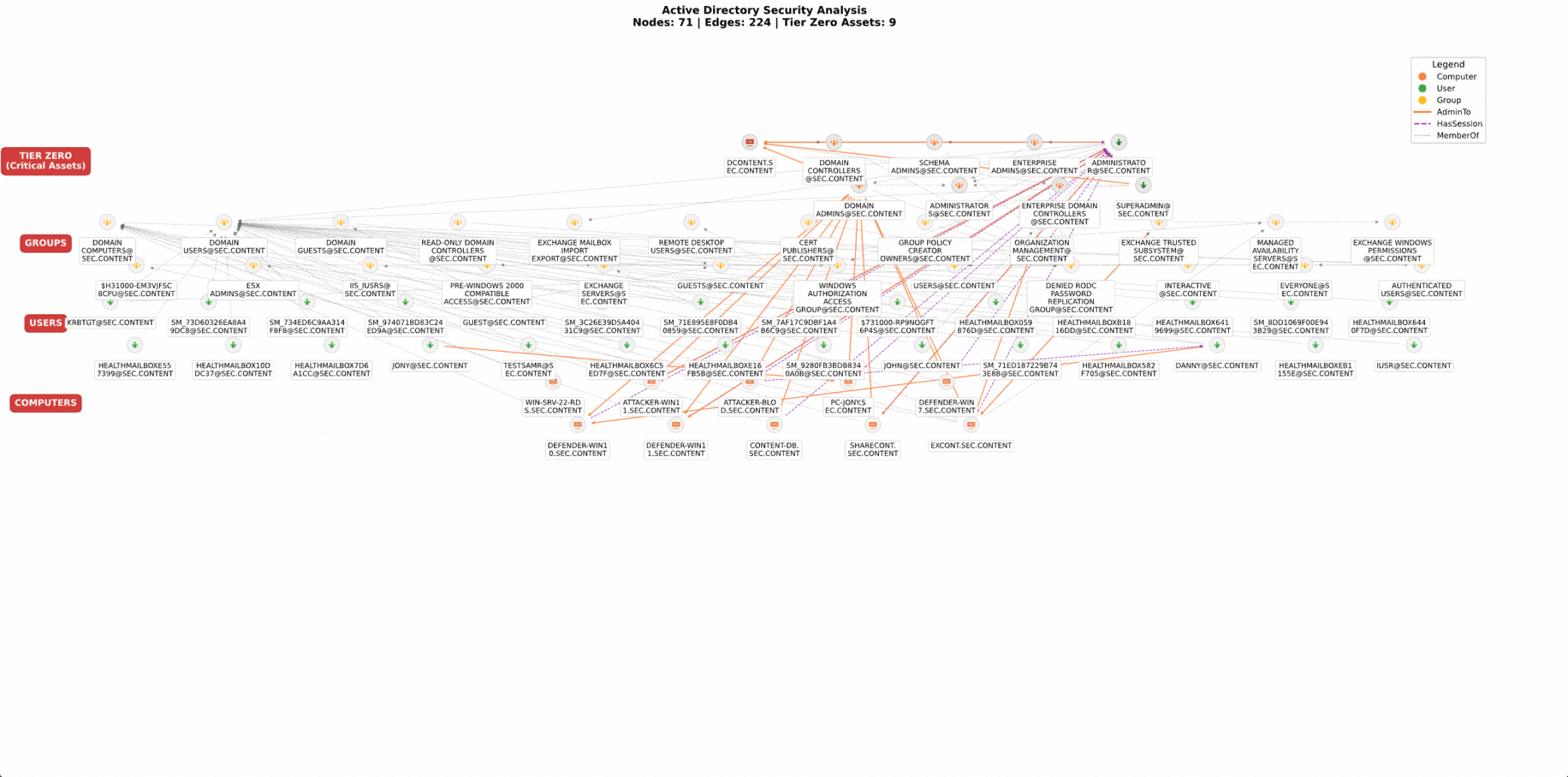
SharpHound has established itself as the backbone of AD discovery, functioning almost as an integrated feature of BloodHound. It collects AD data through three primary Windows data gathering methods: LDAP(s) and SMB with Distributed Computing Environment / Remote Procedure Calls (DCERPC). LDAP queries to Domain Controllers (DCs) enable comprehensive mapping of the AD structure, while SMB-named pipes communicate with network devices to gather detailed permission and session data. SharpHound collects network permissions, user sessions, and group configurations through this process. When visualized in BloodHound, we can uncover critical attack vectors for threat actors while also serving as a forensic tool to identify overprivileged users and devices. In addition to the original SharpHound executable, a PowerShell version offers the same core functionality, suitable for situations where running binaries might raise flags or get blocked. This allows threat actors to blend in or evade detection, especially in environments where script-based tooling flies under the radar.
Figure 1. Lab environment demonstrating the data collected using SharpHound
SoapHound: Extending Beyond AD into Web Services
While SharpHound traditionally uses LDAP for AD enumeration, SoapHound takes a different approach with ADWS, a Microsoft service that allows remote management and querying of AD over HTTP(S). As the name suggests, it uses XML Simple Object Access Protocol (SOAP) messages to communicate with AD. The interface and query syntax remain familiar to LDAP, and it lets you create, modify, and query AD objects.
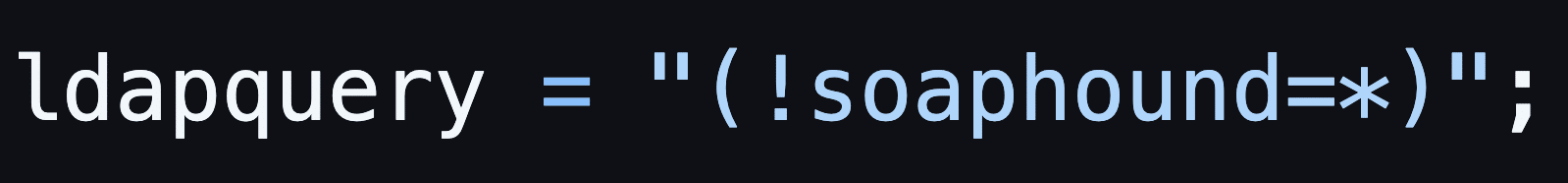
SoapHound has three main capabilities. The primary one is collecting BloodHound-compatible data, which gathers naming attributes, security access control, authentication tracking, and Group Policy information. Instead of using a generic query for the entire domain, SoapHound uses an obfuscated LDAP query, hiding its real intention. Querying everything inside the domain that is not SoapHound.
Figure 2. SoapHound obfuscating its LDAP query
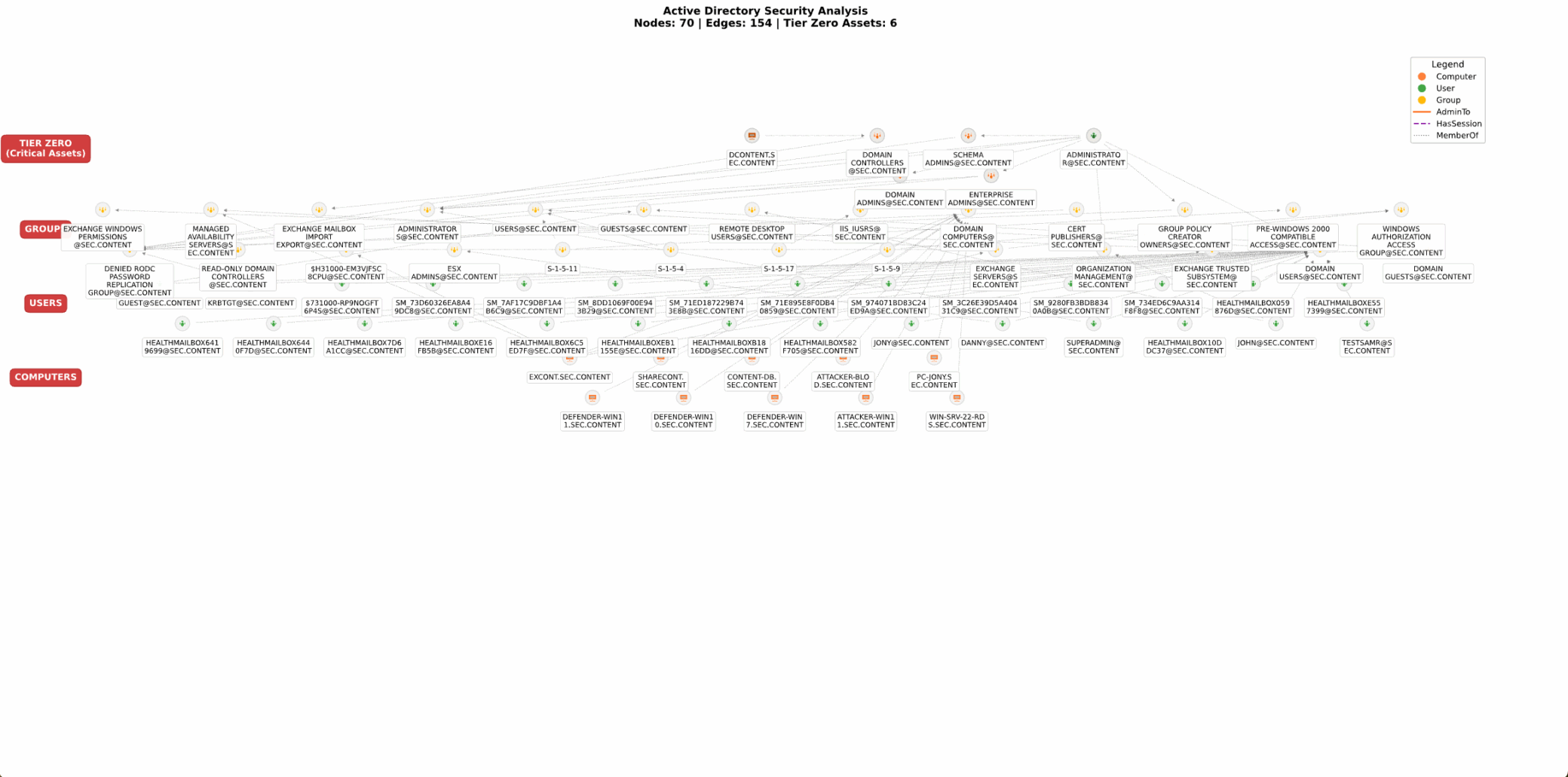
Other capabilities include harvesting certificate templates and DNS nodes from the DC, providing deeper insight into potential attack surfaces. Certificate templates can reveal misconfigurations in Active Directory Certificate Services (AD CS), which threat actors may abuse to forge authentication or escalate privileges. On the other hand, DNS nodes expose the internal naming structure of the domain, helping threat actors identify key systems, locate domain controllers, and map out paths for lateral movement or persistence.
Figure 3. Lab environment demonstrating the data collected using SoapHound
ShadowHound: It’s All About Stealth
ShadowHound is a lightweight alternative to SharpHound and SoapHound. Unlike SoapHound (which exclusively uses ADWS) or SharpHound (which exclusively uses LDAP), ShadowHound offers flexibility by supporting LDAP and ADWS-based AD enumeration from the DC.
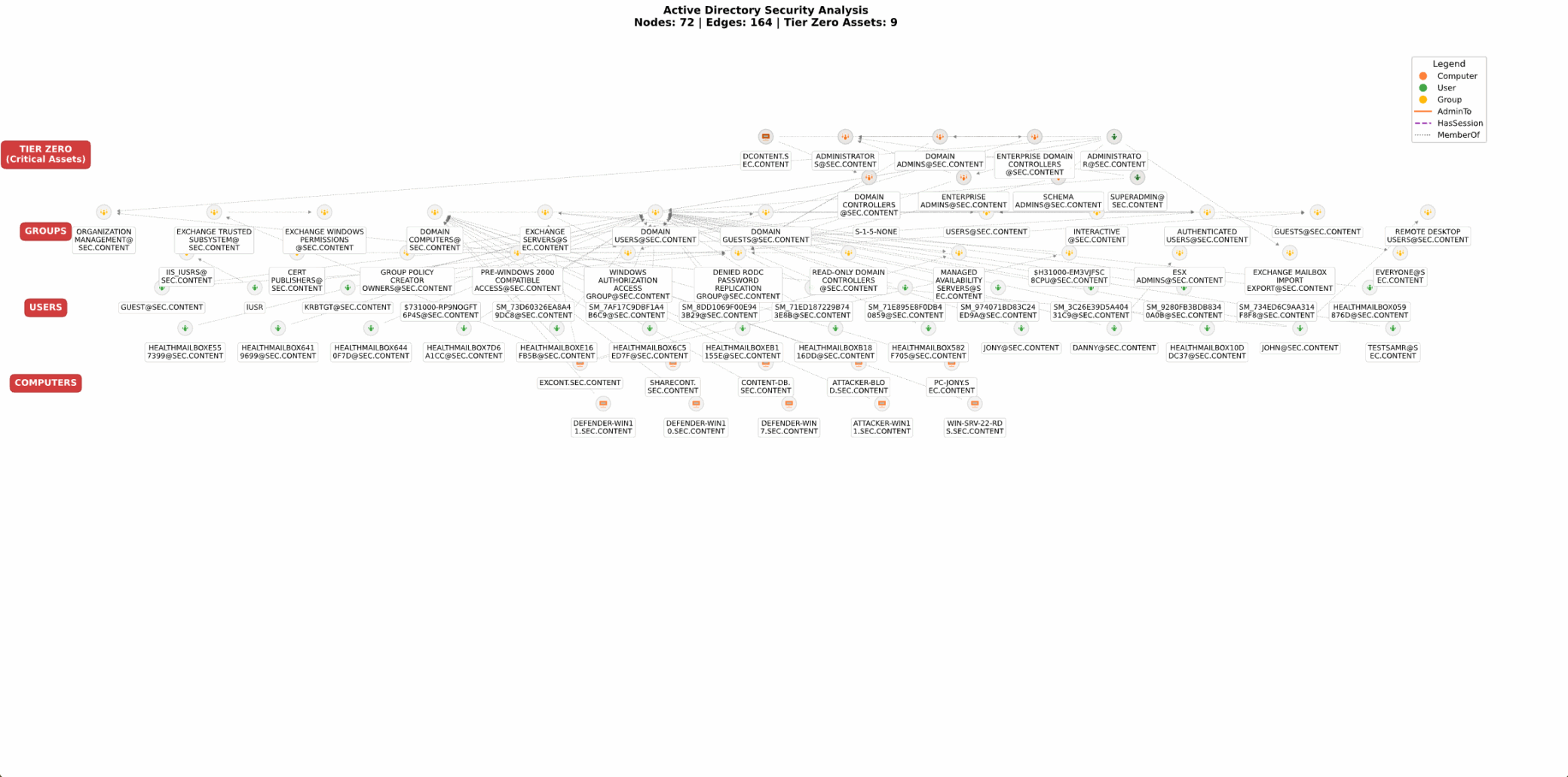
By default, ShadowHound performs recursive queries on the entire AD tree using (objectGuid=*), gathering all available property data. It matches SoapHound’s certificate enumeration features, supporting LDAP and ADWS in collecting information about enrollments, templates, and certificate authorities.
Figure 4. Lab environment demonstrating the data collected using ShadowHound
Key Comparison
SharpHound
What truly sets SharpHound apart is its ability to reach beyond the DC, extending deep into the network infrastructure. While other tools stop at DC enumeration, SharpHound leverages SMB pipes (samr, srvsvc, winreg, lsarpc, and wkssvc) to connect with discovered endpoints in the network. This network-wide reach enables SharpHound to collect critical data that other Hounds don’t reach, including user session details, logged-on users, active sessions, group policy configurations, and host-device permissions.
2025 Cato CTRL Threat Report | Download the report
Threat Report | Download the report
SoapHound
While SharpHound relies on LDAP, SoapHound uses ADWS-based enumeration, providing an alternative path for gathering AD data when LDAP-focused detection mechanisms are in place. Though ShadowHound later implemented similar ADWS capabilities, SoapHound notably stands alone in its ability to perform comprehensive DNS record dumping.
ShadowHound
Unlike SoapHound, which requires compiled executables, ShadowHound implements its functionality through PowerShell scripts while supporting LDAP and ADWS protocols. Why use binaries usually detected by EDR tools when you can use PowerShell to achieve the same results more stealthily? This PowerShell-based approach allows easier customization and integration into existing automation workflows.
Practical Benefits
Detection and Evasion
SharpHound
Detecting SharpHound is challenging due to its reliance on a common integrated enumeration method, which blends its activity into legitimate network operations. However, defenders can spot its execution timeframe and the high volume of queries it generates. SharpHound also supports a “stealth mode” that reduces its footprint by limiting LDAP queries.
SoapHound
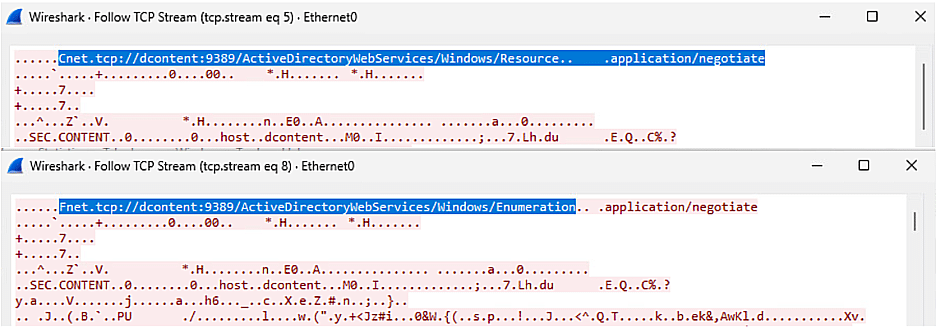
Although SoapHound operates over encrypted ADWS, its command executions remain unencrypted and detectable in network logs. Security teams can monitor unusual ADWS queries or look for anomalies in SOAP request patterns to identify potential reconnaissance attempts.
Figure 5. SoapHound initiating enumerations in ADWS
ShadowHound
ShadowHound’s PowerShell scripts are less noticeable on endpoints, but they perform with extensive LDAP queries to the DC, making it evident on the network. Like its predecessors, ShadowHound can operate more stealthily using targeted LDAP queries.
Conclusion
BloodHound collectors, including SharpHound, SoapHound, and ShadowHound, are all about visibility. Each collects data differently: SharpHound uses built-in protocols, SoapHound leans on API calls, and ShadowHound combines both for broader coverage. But the goal is the same: map out who can do what, where, and how it can be abused. Red teams should use them to cut through the noise and plan exact attack paths. Blue teams should do the same to shut those paths down before using them. The real danger often isn’t flashy exploits, but quiet misconfigurations, over-permissioned accounts, and old trust relationships. These tools shine a light on all of them. Knowing how they work isn’t just helpful, it’s how defenders can stay ahead.
The post Cato CTRL™ Threat Research: Overview of BloodHound and Associated Collectors Including ShadowHound, SharpHound, and SoapHound appeared first on Cato Networks.