Cato CTRL™ Threat Brief: “React2Shell” Vulnerability Targeting React Server Components
Executive Summary
On Wednesday, December 3, a critical remote code execution (RCE) vulnerability in React Server Components (RSC), dubbed React2Shell (CVE-2025-55182), was disclosed. The CVE was discovered by security researcher Lachlan Davidson. It quickly gained traction with multiple third-party proof of concepts (PoCs) being published of varying quality and credibility.
This grace period, during which an official PoC was not available, was a gift for defenders. As a result, the rush-to-patch began, but so did the rush-to-pwn. Once accurate PoCs were released by security researcher Moritz Sanft and Davidson on Friday, December 5 on GitHub (here and here), blind scanning and exploit attempts ramped up sharply. According to the Amazon threat intelligence team, there have been “active exploitation attempts by multiple China state-nexus threat groups, including Earth Lamia and Jackpot Panda.”
Since the vulnerability disclosure on December 3, Cato CTRL has observed more than 10,000 React2Shell attacks mostly originating from Bulgaria, Germany, Laos, Netherlands, Poland, and United States. The top affected sectors include manufacturing, healthcare, technology, construction, and consumer goods.
React2Shell is present in versions 19.0, 19.1.0, 19.1.1, and 19.2.0 of:
- react-server-dom-webpack
- react-server-dom-parcel
- react-server-dom-turbopack
React2Shell has also been confirmed to affect the following React-based frameworks: Next.js, Vite and Parcel RSC Plugins, Redwood SDK, Waku, and React Router. It is likely that additional frameworks and products relying on RSC are also impacted.
Cato’s own SASE infrastructure was not affected by this vulnerability.
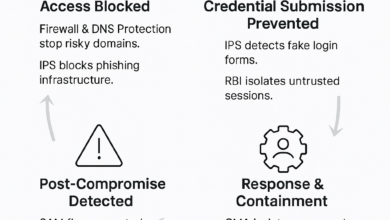
With React2Shell, Cato delivers the following protections to customers:
- Early React2Shell variants were blocked by existing Cato IPS signatures.
- On the day each new PoC was released, dedicated Cato IPS signatures for React2Shell variants were deployed across the Cato SASE Cloud Platform.
2025 Cato CTRL Threat Report | Download the report
Threat Report | Download the report
Technical Overview
React Server Components Unsafe Deserialization: A Prime Attack Surface
React Server Components (RSC), officially released as part of React version 19.0.0, are used by applications to render data on the server-side rather than the client app, boosting performance and reducing JavaScript bundle sizes.
In order to send server-rendered component data to clients, a serialization protocol called React Flight was introduced alongside RSC.
Data serialization is the process of converting complex data structures into a streamlined format that can be easily stored, transmitted, and later reconstructed into its original form. This process exists in other programming languages under different names, such as Pickling (Python) and Marshalling (DotNet).
React2Shell stems from the unsafe deserialization process performed by the server through React Flight. Due to insufficient validations on the serialized data, threat actors can leverage this process in order to execute arbitrary code on the server.
Prototype Pollution: Adding Insult to Injury
While deemed optional through the official PoCs released by Davidson, the recreated PoC by Sanft showcases a subset of the vulnerability, in which another primitive called prototype pollution is leveraged.
Prototype pollution is a JavaScript vulnerability, which stems from its object-oriented structure and property inheritance. An object prototype is an internal reference to another object from which it inherits properties and methods.
Prototype pollution is a process in which threat actors reference an object prototype to access arbitrary properties and methods, which were not intended for use in that specific vector, and it usually stems from insufficient validation of user input.
Cato CTRL’s Observations of React2Shell Activity in the Wild
Following the disclosure on December 3, Cato CTRL observed low-volume probes, based on the AI-generated PoC, originating mostly from the public internet protocol (IP) space in India. These were soon followed by broad automated scanning that appeared to originate from common vulnerability-scanning infrastructure, with source IPs concentrated in countries such as Germany, Netherlands, and United States.
As more reliable PoCs emerged, we started observing high-volume exploitation attempts. Many of these originated from virtual private servers (VPS) and hosting environments, including providers with presence in Bulgaria, Laos, and Poland, , which are often used for both legitimate security research and abuse. These attempts also included a wider range of payloads being used:
- Forced JS error invocation (likely used to match vulnerable servers)
- Asynchronous function invocations
- Defence evasion attempts using unicode encoding
- JS networking primitives loaded in memory
This payload diversity demonstrates just how many paths a threat actor can take when exploiting a single, well-placed RCE vulnerability-from simple denial of service (DoS) attacks to malware deployment and data exfiltration.
Another interesting observation was that most exploits were adopting the recreated PoC by Sanft, which included the optional prototype pollution technique. This is likely since it was published and quickly adopted before Lachlan’s official PoC.
The top affected sectors include manufacturing, healthcare, technology, construction, and consumer goods.
This progression from early copy-paste PoCs to diverse automated probing and tailored payloads highlights how quickly server-side vulnerabilities of this class move from disclosure to internet-wide activity, and why Cato CTRL continuously tracks emerging exploit attempts to keep protections up to date.
Conclusion
React2Shell is an interesting use-case that combines known primitives, a widely adopted attack surface, and ease of exploitation. That said, it is not the first and will certainly not be the last.
Now more than ever, it is clear that organizations must stay ahead of the curve by establishing robust defences before new attacks are published, as well as closely monitoring emerging threats.
Protections
With React2Shell , Cato delivers the following protections to customers:
- Early React2Shell variants were blocked by existing Cato IPS signatures.
- On the day each new PoC was released, dedicated Cato IPS signatures for React2Shell variants were deployed across the Cato SASE Cloud Platform.
The post Cato CTRL™ Threat Brief: “React2Shell” Vulnerability Targeting React Server Components appeared first on Cato Networks.