Vendor News
Category Added in a WPeMatico Campaign
-
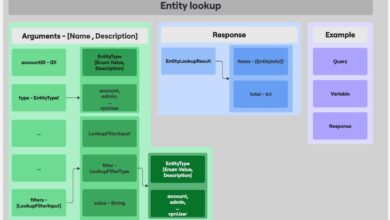
Introducing Cato’s API Assistant: Your New Copilot for GraphQL
Imagine you just got a new car with a feature that automatically adjusts the air conditioning based on live weather…
Read More » -
Cato CTRL™ Threat Research: Oyster Malware Loader Targets Tech-Savvy Users with Smarter Techniques During Summer Malvertising Campaign
Executive Summary Summertime in the U.S., Europe, and many other regions typically falls between June and September. Tech teams, admins,…
Read More » -
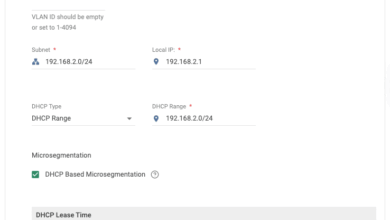
One Click to Zero Trust: How Cato’s Agentless Microsegmentation Blocks Lateral Movement and Simplifies Network Security
One click on a malicious email. One compromised device. That’s often all it takes for malware or ransomware to spread…
Read More » -
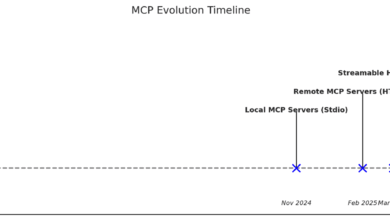
Designing the Future of Agentic AI: Cato Engineering Details a New Practical, Secure, and Scalable MCP Server Framework
Some of you may remember the early days of security, when setting up a firewall or antivirus felt like enough.…
Read More » -
Security and Performance Issues, Handled: The Efficiency Power of Cato XOps
Imagine Your Undersized Team Has Just Missed That One, Critical Alert Among Millions You’re an IT professional whose teams manage…
Read More » -
Cato CTRL™ Threat Research: New Streamlit Vulnerability Enables Cloud Account Takeover Attack and Stock Market Dashboard Tampering
Executive Summary Imagine financial analysts watching stock prices suddenly drop. Dashboards show misaligned data, market confidence disappears, and trading screens…
Read More » -
ZTNA Alone Won’t Win the Zero Trust Race. Here’s Why.
In the race to secure modern enterprises, Zero Trust Network Access (ZTNA) is gaining speed, and has become the default…
Read More » -

Cato CTRL™ Threat Brief: “ToolShell” Exploit Targeting Microsoft SharePoint Vulnerabilities
Executive Summary On July 22, 2025, Microsoft published an overview of a series of critical vulnerabilities affecting Microsoft SharePoint Server…
Read More » -

Cato CTRL™ Threat Research: Analyzing LAMEHUG – First Known LLM-Powered Malware with Links to APT28 (Fancy Bear)
Executive Summary On July 17, 2025, Ukraine’s Computer Emergency Response Team (CERT-UA) publicly reported LAMEHUG, which is being documented as…
Read More » -

Inside Qubit Conference Prague 2025: Hacking Social Platforms and Securing AI
Qubit Conference Prague 2025 brought together some of the sharpest minds in cybersecurity—and Cato CTRL made sure to leave a…
Read More »