-
Vendor News

Cato CTRL™ Threat Brief: “ToolShell” Exploit Targeting Microsoft SharePoint Vulnerabilities
Executive Summary On July 22, 2025, Microsoft published an overview of a series of critical vulnerabilities affecting Microsoft SharePoint Server…
Read More » -
Vendor News

Cato CTRL™ Threat Research: Analyzing LAMEHUG – First Known LLM-Powered Malware with Links to APT28 (Fancy Bear)
Executive Summary On July 17, 2025, Ukraine’s Computer Emergency Response Team (CERT-UA) publicly reported LAMEHUG, which is being documented as…
Read More » -
Vendor News

Inside Qubit Conference Prague 2025: Hacking Social Platforms and Securing AI
Qubit Conference Prague 2025 brought together some of the sharpest minds in cybersecurity—and Cato CTRL made sure to leave a…
Read More » -
Vendor News

Cato CTRL™ Threat Research: Investigation of RMM Tools Leveraged by Ransomware Gangs in Real-World Incidents
Executive Summary Remote Monitoring and Management (RMM) tools are essential for IT operations, but their powerful capabilities and trusted status…
Read More » -
Vendor News

Cato CTRL™ Threat Actor Profile: IntelBroker
Executive Summary In June 2025, FBI New York and the U.S. Attorney’s Office for the Southern District of New York…
Read More » -
Vendor News

A Leader Once Again: Cato Networks Recognized in 2025 Gartner® Magic Quadrant™ for SASE Platforms
For the second consecutive year, Cato Networks has been recognized as a Leader in the 2025 Gartner® Magic Quadrant for…
Read More » -
Vendor News
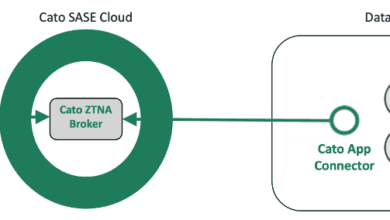
Cato’s Unique ZTNA Broker Architecture – A Difference That Matters!
Zero Trust Network Access (ZTNA) has rapidly become a foundational security strategy for organizations modernizing their IT infrastructure. The increasing…
Read More » -
Cato CTRL™ Threat Research: Overview of BloodHound and Associated Collectors Including ShadowHound, SharpHound, and SoapHound
Executive Summary Think back to when you were a kid, eyeing a cookie jar on the top shelf. Getting to…
Read More » -
How Partners Can Lead with Cato
To compete in today’s retail landscape, IT must support new growth strategies while delivering seamless, secure customer experiences. This means…
Read More » -
Rewriting the Rules of China Connectivity with Cato SASE Cloud
What if operating in China didn’t require a separate architecture? For global enterprises, China is too important and too complex…
Read More »