Cato CTRL™ Threat Research: Preventing Privilege Escalation via Active Directory Certificate Services (ADCS)
Executive Summary
Maintaining an Active Directory (AD) enterprise environment is no easy task. Between all the permissions, security compliances, update cycles, emergency patches, appliance configurations and more, covering all the bases could feel overwhelming at times and could lead to errors that may result in major consequences.
For example, in the scope of authentication and credential management, IT admins tend to invest their efforts in password management policies, defining standards for password strength, storage solutions and rotation schedules.
At the same time, alternative authentication methods, such as certificate-based authentication, which offer a wide array of configurations, don’t get the same level of attention to details and corresponding policies. This has led to extensive research into Active Directory Certificate Services (ADCS), highlighting this impactful and often overlooked privilege escalation surface.
By leveraging misconfigurations in ADCS implementations, threat actors are able to escalate their privileges and impersonate high-value domain accounts, up to and including domain admins, possibly leading to full domain compromise.
This ever-growing attack surface has racked up 16 unique privilege escalation techniques (ESC1-16), with Certipy providing a summary of those techniques, and that number will likely increase over time. Furthermore, recent research from BeyondTrust, presented at SO-CON 2025, showcases how these on-premises misconfigurations can even lead to a full compromise of cloud-based infrastructure on hybrid implementations.
The Cato SASE Cloud Platform provides enterprises with the ability to detect and prevent ADCS exploitation by identifying known exploitation techniques as well as raising alerts on suspicious certificate-related network activity.
Technical Overview
According to Microsoft, “Active Directory Certificate Services (ADCS) is a Windows Server role for issuing and managing public key infrastructure (PKI) certificates, used in secure communication and authentication protocols.”
The digital certificates issued by an ADCS server are used for the encryption and signing of documents and network traffic, as well as the authentication of entities in the domain (such as users and computers). These same certificates are commonly issued based on pre-existing certificate templates that define the rules for certificate issuance, such as:
- Extended Key Usage (EKU): What activities can the certificate be used for?
- Enrollment Permissions: Who can enroll for the certificate?
- Whether the certificate requires CA manager approval or is auto-approved
- Any number of arbitrary configurations
These templates, created by system administrators, are one of the main surfaces abused through multiple ESC techniques, while additional misconfigurations are also found on Certificate Authority (CA) servers, Domain Controllers (DCs) and within AD objects.
As of August 2025, 16 unique techniques for ADCS exploitation have been identified, with Certipy providing a summary of those techniques. While there are some differences between them, they all share the same end-goal: privilege escalation leading to lateral movement, persistence and even full domain compromise.
For a quick reference, the appendix table at the end of this article lists all 16 techniques, grouped by their underlying attack surface.
2025 Cato CTRL Threat Report | Download the report
Threat Report | Download the report
The Threat Actor’s Toolbox
As part of continuous research into this attack surface since its initial publication, several tools were developed for exploitation and reconnaissance. Most tools don’t provide coverage for all 16 ESC techniques and only offer some of the utilities required for an end-to-end privilege escalation.
Most notable in our view is Certipy, a Python-based open-source toolkit for enumerating and exploiting ADCS, created to help red teams, penetration testers and defenders. It can be used to detect misconfigurations, but also to issue certificates utilizing a large range of escalation techniques and leveraging them for domain authentication. Lastly, it provides very detailed documentation for each technique, including command line syntax, expected output, mitigation techniques and more.
Other notable tools are:
- Metasploit Framework: The Metasploit Framework provides modules for multiple escalation techniques and is leveraged to gain authentication, but it has less of a variety than what Certipy provides.
- Certify: This C#-based tool for ADCS abuse and enumeration was created alongside the Certified Pre-Owned whitepaper and blog. A new version of the tool (Certify 2.0) was released on August 11, 2025, refreshed with enhanced capabilities.
- Certreq.exe: This built-in Windows command-line tool can be used to request, retrieve and accept digital certificates. Since it is an integral part of the Windows operating system (OS), it can be used in a living-off-the-land approach to issue certificates based on misconfigurations, but the tool lacks the capability of authenticating in the domain.
ESC1 Attack Demo
Now that we’re familiar with the different ESC attacks, and the available tools, let’s break down a full end-to-end attack:
To Entra and Beyond
While organizations all over the world are transitioning towards cloud-based infrastructure, hybrid implementations are becoming very common. These implementations combine both on-premises systems, like servers and datacenters, with cloud-based services in order to balance compliance, legacy support, scalability and cost.
One of the key components within such setups is Identity and Access Management (IAM). Microsoft Entra ID (formerly known as Azure AD) is Microsoft’s implementation of an IAM service, providing authentication, authorization and identity management across cloud-based and on-premises infrastructures. For our purposes, it’s important to note that this service includes a certificate-based authentication called Microsoft Entra Certificate-Based Authentication (CBA).
In plain words, this suggests that a threat actor who successfully retrieved a certificate signed by the on-prem ADCS server can extend the trust between Entra CBA and the on-premises public key infrastructure (PKI) in order to move laterally to the cloud.
Recent research from BeyondTrust, presented at SO-CON 2025, showcases this exact attack vector, as well as potentially similar implications for other services.
Proactive Defense: Identifying Misconfigurations
As seen in the demo, when abusing ADCS for privilege escalation, the first step for threat actors after initial access is usually enumeration. Threat actors need to enumerate the certificate templates available for their compromised user as well as other AD attributes, in order to determine whether any of the ESC techniques is viable.
Rather than waiting for the inevitable, here’s how you, as a defender / system administrator, can leverage Certipy’s enumeration utilities to strengthen your security posture:
The following command leverages Certipy to enumerate misconfigurations in ADCS, generating an output file which references their corresponding ESC techniques:
Certipy find -u ‘[email protected]’ -p ‘UserPassword’ -dc-ip ’10.0.01’ -text -enabled -hide-admins
Flags used:
-u: Username for authentication
-p: User password for authentication
-dc-ip: Domain Controller IP address
-text: Output results as formatted text
-enabled: Only show certificate templates published by a CA
-hide-admins: Omit administrator permissions from the output
For example, the following output was produced for our vulnerable template:
In addition to the overview of relevant ESC attacks, it will list key settings like certificate template Extended Key Usage (EKUs) and enrollment rights, allowing for a centralized inspection of all relevant data.
If all else fails, following these guidelines when configuring your ADCS PKI implementation should minimize the attack surface and help contain lateral movement and privilege escalation scenarios:
- Disable unused resources, such as certificate templates and enrollment interfaces.
- Keep enrollment rights on certificate templates to a minimum.
- Avoid NTLM authentication for sensitive resources like ADCS.
- Audit & monitor sensitive operations. A full list of related Windows events is detailed in Microsoft’s documentation.
Protections
The Cato SASE Cloud Platform amplifies an enterprise’s ability to detect and prevent ADCS exploitation by identifying certificate enrollment requests and certificate-based authentication attempts, generating contextual events:
- Cato IPS helps identifying and preventing the use of known ADCS exploitation tools, including the recently released Certify 2.0.
- Cato’s Suspicious Activity Monitoring (SAM), a feature within Cato IPS, helps detecting abnormal certificate-related network activity.
Conclusion
Understanding how ADCS operates, as well as the risks imposed by the many misconfigurations which are bound to take place in such infrastructure sooner or later, is crucial for strengthening an organization’s security posture.
Implementing routine verification checks of critical settings across all levels of the public key infrastructure, from certificate templates to domain objects and certificate authority (CA) settings, as well as monitoring critical activities such as Certificate Signing Requests (CSR) and Kerberos PKINIT authentication requests, should be considered a top priority for any organization using ADCS for certificate management in their domain, affecting even cloud-based infrastructure through hybrid implementations.
Appendix: Understanding the Different ESC Attacks
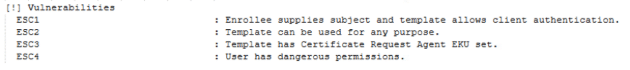
Techniques: ESC1, ESC2, ESC3, ESC9, ESC13
- Attack Surface: Misconfigured Certificate Templates
- Description:
- Through these techniques, threat actors abuse certificate templates which don’t require manager approval and include enrollment rights for low privileged users / groups.
- The main differences here are the different template settings being abused:
- ESC1 abuses templates with authentication EKUs that also allow the Subject Alternative Name (SAN) to be specified by the certificate requester.
- ESC2 abuses templates with the any-purpose EKU / no EKU.
- ESC3 abuses templates with the enrollment-agent EKU, using those to enroll for other certificates.
- ECS9 abuses templates without a security extension. This extension was introduced by Microsoft to enable strong certificate mapping, which allows DCs to map certificates to specific user / computer accounts in AD based on their Security identifiers (SID).
- ESC13 abuses templates containing an issuance policy object identifier (OID), which is linked to a specific AD security group through AD configuration. A template’s issuance policy is a set of rules / restrictions applied by the CA to determine how certificates are issued and represented in templates as OIDs. The result is a certificate being issued with the privileges of that AD security group, and all groups it is a member of, even if the requester is not part of those groups.
Techniques: ESC4, ESC5, ESC7, ESC14
- Attack Surface: Misconfigured Active Directory Objects
- Description:
- Through these techniques, threat actors can abuse misconfigurations in various AD objects for privilege escalation and impersonation. In addition, threat actors with ‘write’ access for specific AD objects can modify those objects, actively introducing misconfigurations into a previously secure environment.
- The main difference here is the modified object:
- ESC4 abuses certificate template objects, turning previously secure templates vulnerable to other techniques.
- ESC5 abuses various PKI objects, resulting in unauthorized certificates issuance, denial of service (DOS), persistence and even full control over the domain.
- ESC7 abuses the CA object or its services directly, resulting in full CA control, unauthorized certificate issuance and full domain compromise.
- ESC14 abuses the altSecurityIdentities attribute in AD user / computer accounts, which allows administrators to manually map these accounts to specific certificates for authentication. If this explicit mapping is flawed (for example, it can be easily guessed or relies on spoofable certificate components / non-unique certificate fields), threat actors can obtain or forge a matching certificate to impersonate the linked AD account.
Techniques: ESC6, ESC15, ESC16
- Attack Surface: Misconfigured / Vulnerable Certificate Authority Servers
- Description:
- Through these techniques, threat actors directly abuse misconfigurations or exploit vulnerabilities in the CA server.
- ESC6 abuses the same setting as ESC1 (client-specified SAN), but configured globally on the CA instead of a specific template. Thus, acting as a CA-wide override.
- ESC15, also known as EKUwu or CVE-2024-49019, refers to the exploit of a vulnerability in unpatched CA servers, allowing threat actors to inject arbitrary application policies into certificates based on V1 schema templates. This technique is usually combined with an threat actor-specified SAN (similarly to ESC1) and used to inject EKUs associated with ESC1-3.
- ESC16 abuses the same setting as ESC9 (missing security extension), but configured globally on the CA instead of a specific template. Thus, acting as a CA-wide override.
Techniques: ESC8, ESC11
- Attack Surface: NTLM Relay to ADCS
- Description:
- Through these techniques, threat actors coerce legitimate users to authenticate to their machine, then relay those authentication requests to the ADCS server’s certificate enrollment interfaces, essentially impersonating those users and enrolling for certificates in their name. The main difference here is the ADCS enrollment interface used:
- ESC8 relays authentication requests to the web enrollment interface (HTTP-based).
- ESC11 relays authentication requests to the RPC-based enrollment interface.
- NTLM relay to ADCS has been incorporated in widely known exploit-chains, such as PetitPotam (CVE-2021-36942).
- Through these techniques, threat actors coerce legitimate users to authenticate to their machine, then relay those authentication requests to the ADCS server’s certificate enrollment interfaces, essentially impersonating those users and enrolling for certificates in their name. The main difference here is the ADCS enrollment interface used:
Techniques: ESC10
- Attack Surface: Misconfigured Server Authentication Settings
- Description:
- Through this technique, threat actors can abuse the Windows Secure Channel (Schannel) security package configuration, used for transport layer security (TLS) authentication in services like Hypertext Transfer Protocol Secure (HTTPS) and Lightweight Directory Access Protocol Secure (LDAPS). This security package maps certificates to domain accounts based on a registry key on the server, which can be configured to map based on the UserPrincipalName (UPN) attribute of an AD account. Threat actors with the permissions required to change their account’s UPN can abuse this config in order to authenticate as a different AD account.
- This technique is similar in concept to ESC1 & ESC9, in both user impersonation and the bypass of Microsoft’s strong certificate mapping (primarily designed for Kerberos PKINIT authentication).
Techniques: ESC12
- Attack Surface: Abuse YubiHSM2
- Description:
- YubiHSM2 is a hardware device used to protect a server’s cryptographic keys. This technique targets ADCS servers using vulnerable YubiHSM2 devices to store and manage their private signing keys and requires pre-existing shell access on the CA server for a low-privileged user.
- This scenario is only relevant for very specific implementations. It is included in ADCS threat vector discussions for completeness reasons, but its classification as an ESC attack is debatable.
The post Cato CTRL™ Threat Research: Preventing Privilege Escalation via Active Directory Certificate Services (ADCS) appeared first on Cato Networks.