Cato’s Unique ZTNA Broker Architecture – A Difference That Matters!
Zero Trust Network Access (ZTNA) has rapidly become a foundational security strategy for organizations modernizing their IT infrastructure. The increasing distribution of users, devices, and applications makes traditional security measures inadequate. Several solutions offer cloud-based brokers to implement ZTNA, but it’s crucial to understand that these solutions are not created equal. Let’s explore why Cato Networks’ cloud-based ZTNA solution distinctly stands apart.
The Essentials of Cato’s Cloud-Based Broker Architecture
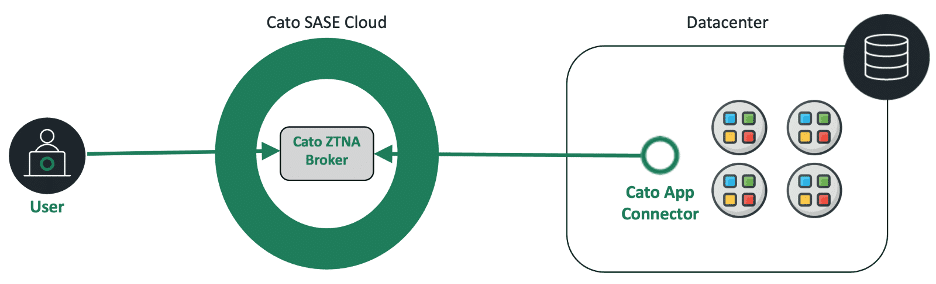
Cato Networks leverages its robust SASE Cloud architecture to implement a secure and scalable ZTNA solution. At its core, the Cato Broker-Connector architecture ensures that only explicitly authorized users gain access to specific private applications without ever exposing the internal network. This contrasts sharply with less secure approaches that risk exposing internal assets to unnecessary threats.
Secure User Access Through Rigorous Authentication
Cato’s approach begins with robust user authentication through methods like Single Sign-On (SSO) and multi-factor authentication (MFA). Users are authenticated by the Cato ZTNA Broker within the secure Cato SASE Cloud, ensuring that no applications are visible or accessible by default. Crucially, user and device postures are continuously assessed, adding an ongoing layer of protection that many simpler ZTNA solutions lack.
Continuous Verification and Risk Management
Cato goes beyond initial authentication and authorization to incorporate continuous verification and dynamic risk management. Every connection request is assessed against granular policies that consider not just identity and role, but also detailed contextual factors such as device posture, user location, network behavior, and current threat intelligence.
Continuous monitoring ensures that risk assessment is an ongoing process rather than a one-time event. If a user’s device posture or behavior changes—such as unexpected geographic location or unusual application activity—the system automatically adjusts permissions in real-time, mitigating potential threats instantly.
Cato’s model leverages policy-driven controls to grant highly precise access, significantly reducing the risk of unauthorized access. Applications are never broadly exposed but are instead dynamically presented only to explicitly authorized users, based on ongoing verification processes.
eBook – ZTNA to Universal ZTNA | Download the eBook
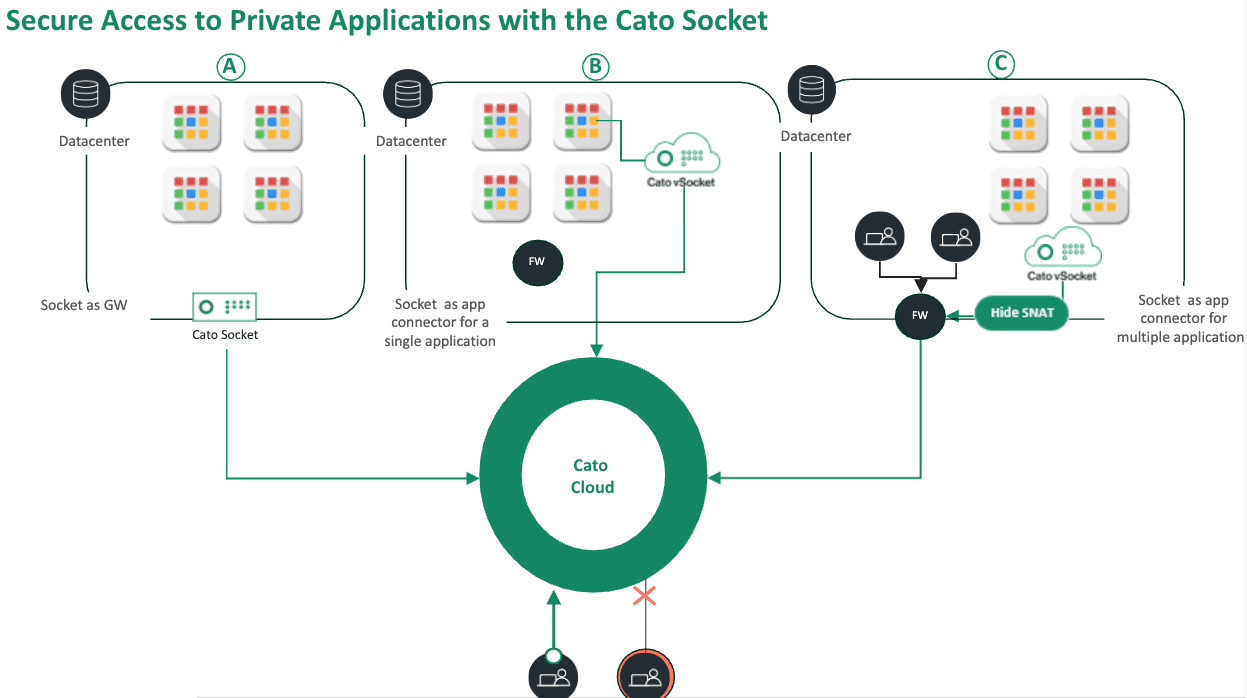
Flexible and Scalable App Connector Models
Unlike solutions with rigid deployment methods, Cato provides flexibility through three distinct App Connector models:
- Connector to All Applications: Ideal for securing broad access to data center resources, benefiting from streamlined connectivity and high performance.
- Connector to a Subset of Applications: Focuses on precise application exposure, significantly reducing risk by isolating access strictly to specified IPs or VLANs.
- Connector to a Single Application: Offers an ultra-lightweight, simple deployment directly on application hosts, suitable for environments needing minimal IT intervention.
These diverse models support both physical and cloud data centers, allowing organizations to adapt swiftly to changing requirements without sacrificing security.
Granular Policy Control and Comprehensive Security Inspection
The Cato ZTNA Broker acts as the secure intermediary, enforcing strict, granular access policies based explicitly on identity, role, device posture, behaviour, and risk. Unlike generic ZTNA solutions that may provide basic access controls, Cato ensures comprehensive security inspection for all application traffic. This includes advanced threat prevention, Cloud Access Security Broker (CASB), Data Loss Prevention (DLP), and rigorous policy enforcement. Thus, traffic is not only controlled but meticulously scrutinized to protect against potential threats comprehensively.
Why Cato Networks Leads the ZTNA Space
Ultimately, the power of Cato Networks’ solution lies in its comprehensive approach. By embedding rigorous security, providing flexible deployment, and ensuring granular policy management, Cato sets itself apart from standard ZTNA offerings.
Organizations looking to secure modern IT environments with agility and scalability should consider a ZTNA solution that provides robust security, flexibility, and cloud-native architecture. Cato Networks offers a differentiated approach designed to meet these critical needs.
The post Cato’s Unique ZTNA Broker Architecture – A Difference That Matters! appeared first on Cato Networks.